
Webinar: Automating Cyber Risk Management Watch the On-Demand Webinar With increasing threats, challenging economic environments, budget limitations, and cyber…
"This is an excellent starting point for any organization that wants to get serious about their cyber risk management. The system has the capability to grow as you become more sophisticated in your use"
IT Director
Services Industry
In the intricate realm of cybersecurity, the need to assess and communicate security effectiveness led to the development of security ratings scales. These scales distill complex security data into a comprehensible format, offering organizations insights into their cybersecurity posture. This article delves into the inner workings of the security ratings scale, shedding light on the factors that contribute to an organization’s overall security rating and understanding how these factors shape the assessment.
At its core, a security ratings scale quantifies an organization’s security posture in a standardized manner. This numerical representation translates intricate security metrics into an accessible form, enabling stakeholders to gauge risk and make informed decisions. Explore more about goes into answering ‘What is a security risk rating?’
The security rating scale can be produced as numerical values (like a credit score) or alphabetic grades, with higher scores or grades indicating better cybersecurity practices and therefore lower cyber risk. The purpose of these scales is to provide a clear, objective, and consistent way to evaluate an organization’s enterprise risk, or vendor cyber risk, and compare the cybersecurity health of different entities where you can monitor their ratings trend over time- and compare to industry benchmarks.
Additional Resources
Context based security ratings
What are security ratings used for?
How are security ratings created?
What is a good cybersecurity rating?
How do you improve your security rating?
Is it easy to switch security ratings providers?
Why is my security rating wrong?
What Kind of Company is BitSight?
Select What are the 5 C’s of Cybersecurity?
What is the Highest Security Rating?
What is the difference between SecurityScorecard and BitSight?
The Evolution of Cybersecurity Ratings and How They Can Boost Risk Visibility

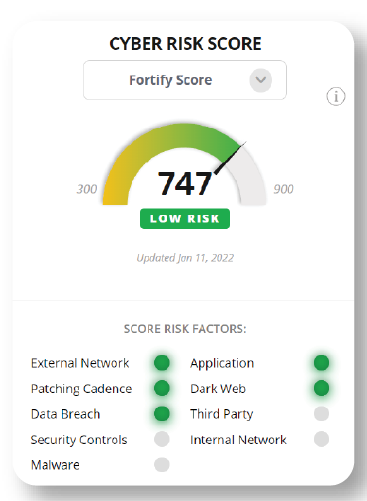
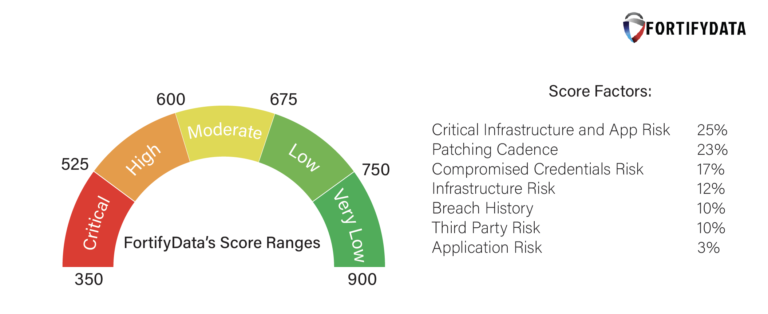
The security ratings scale draws upon a multitude of factors, each contributing to the organization’s overall rating:
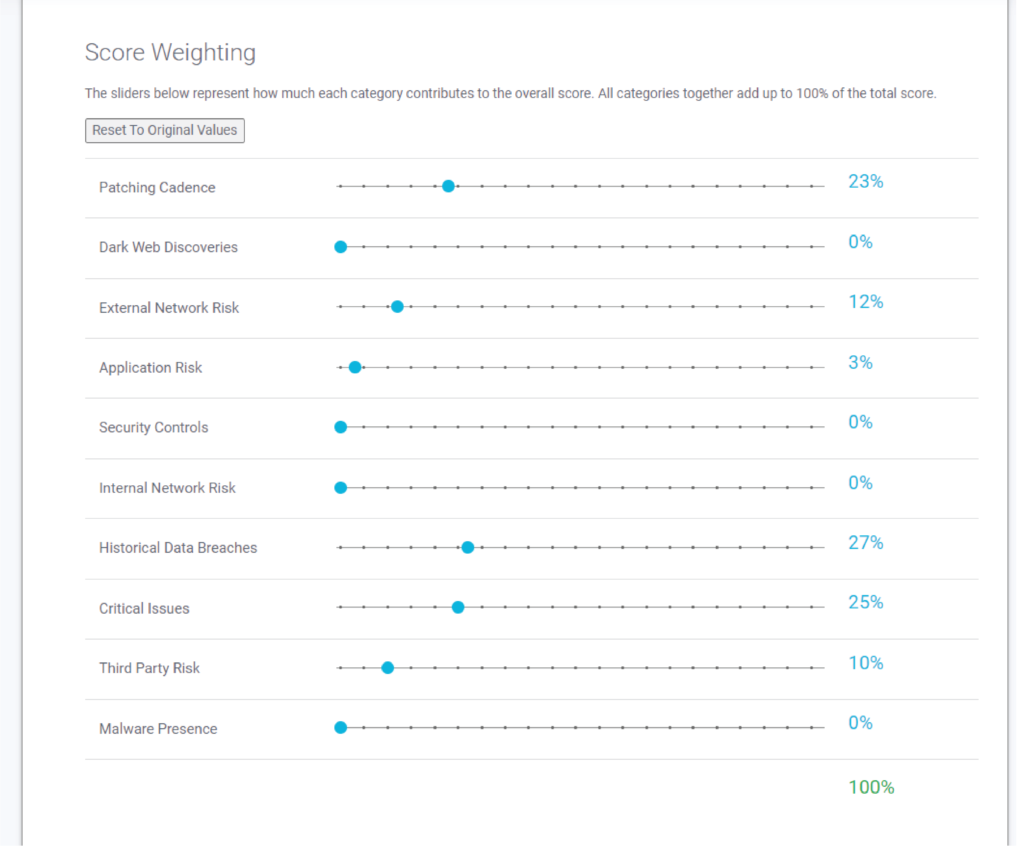
Each of these factors is assigned a weight to reflect its relative importance in assessing the organization’s cybersecurity posture. This weighted data is then aggregated to generate an overall security rating. The methodology used to determine these weights varies between different rating platforms.
FortifyData has made their security rating score methodology publicly available and is the only security rating provider with a patent pending on their configurable security rating risk rating models. Providing adjustable security ratings allows clients to create additional security rating models, in addition to the standard FortifyData score, focused on the factors and weightings of those factors in the score that best address the organization’s specific threat landscape.
Security ratings scales gain depth through relative comparisons. Organizations are often benchmarked against peers within the same industry. This contextual comparison provides a clearer understanding of the organization’s performance compared to similar entities, helping to gauge where improvements are needed.
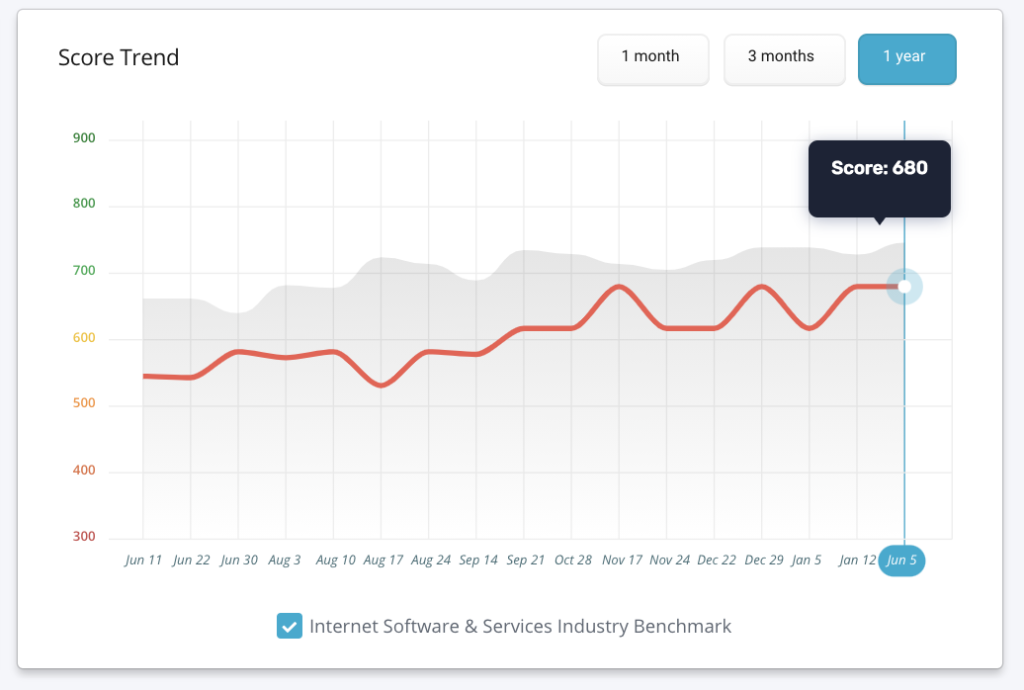
The accuracy and quality of the underlying data sources significantly impact the final rating. Inaccurate or outdated data can lead to a skewed assessment. Therefore, ensuring data accuracy and reliability is crucial for an accurate reflection of the organization’s security posture.
While the security ratings scale offers valuable insights, it’s essential to recognize its limitations. The scale may not fully capture internal security practices and controls that are not publicly disclosed. Additionally, certain factors that contribute to security, such as encryption practices or employee training, may not be accurately reflected.
The security ratings scale offers a structured approach to evaluating an organization’s cybersecurity posture. By understanding the factors that shape the rating, organizations can gain insights into their strengths and vulnerabilities. A comprehensive assessment takes into account various elements, from indicators of compromise to user behavior, allowing organizations to make informed decisions to enhance their security strategy. Embracing the nuances of the security ratings scale empowers organizations to navigate the complex landscape of cybersecurity with a proactive and data-driven approach.


| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |