- Platform
Platforms
- Solutions
- Industries
Industries
- Why FortifyData
Why FortifyData
"This is an excellent starting point for any organization that wants to get serious about their cyber risk management. The system has the capability to grow as you become more sophisticated in your use"
IT Director
Services Industry - Company
Company
- Partners
Partners
- Resources
Resources
The FortifyData Difference
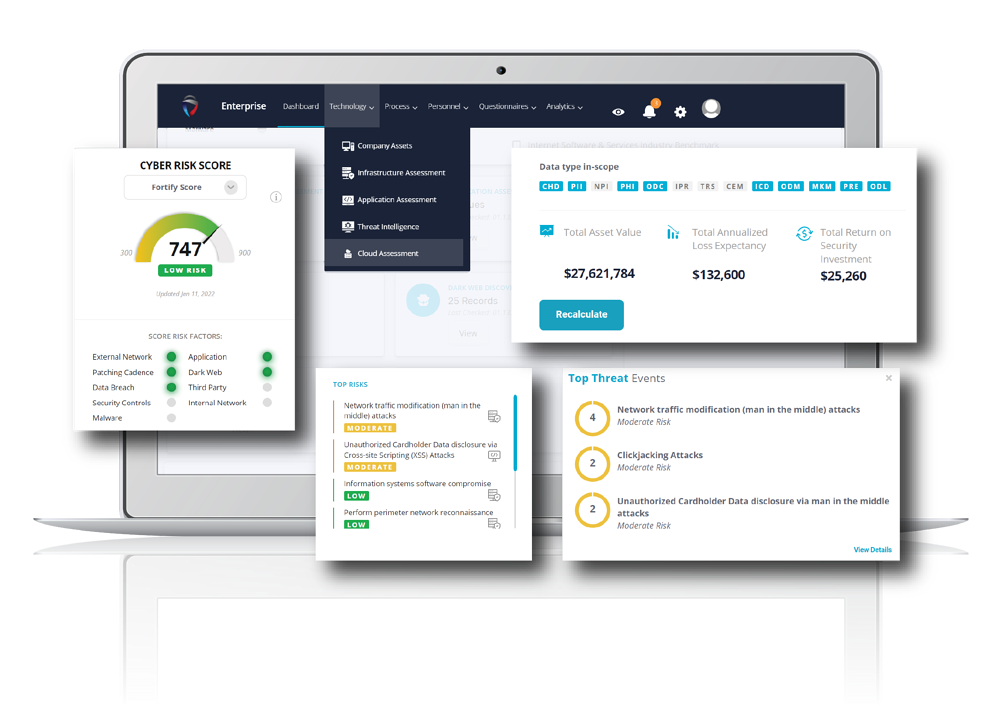
FortifyData has built a Cybersecurity Risk Management platform that enables security leaders and practitioners to identify and manage risk exposures across their entire attack surface – this includes external risks, internal risks, cloud configuration risks, and third-party risks.
All these components are consolidated into one platform that provides more accurate risk insights compared to other solutions in the market. This empowers customers to effectively create best in class Enterprise and Third-Party Risk Management programs with automated live risk informed data. The platform ingests, analyzes, and produces a variety of risk intelligence, including a benchmarked cyber risk rating that incorporates threat and vulnerability data.
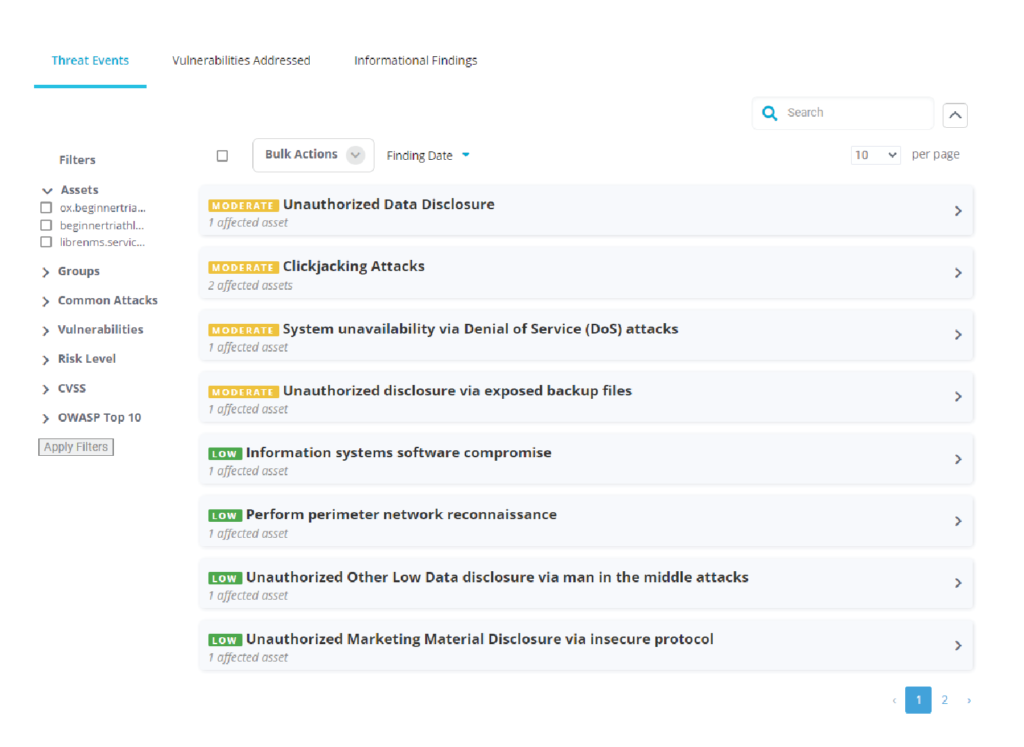
Key Differences
Don’t be limited by an outdated, external-only view of your attack surface. See the benefits of adopting FortifyData’s Cyber Risk Management solution:

Accurate Auto-Asset Discovery
Reduce asset misattributions with FortifyData’s auto asset discovery capability. While other solutions can take up to 4 months to update new asset inventory, we continuously search and identify new assets on a weekly basis.

Data Accuracy
FortifyData collects data through both active and passive assessment methodologies, not relying on historical, OSINT data. We continuously re-assess to make sure all attack surface data is timely and accurate.

Dark Web Intelligence
Our proprietary intelligence feeds alert clients when data has been compromised, either within your organization or through a third-party entity. Through continuous dark/deep web scanning of files and databases across social media, un-indexed and transient deep websites, we will alert you of exposed company records, including leaked information, stolen credentials and confidential documents.

Infrastructure Security Assessment
We conduct full and continuous vulnerability assessments of your internal and external infrastructure. These non-intrusive scans send transmissions to the network’s nodes, uncovering weaknesses. This assessment provides insight on a company’s infrastructure security risks, allowing you to quickly and accurately identify, investigate and prioritize.

Cloud Configuration
Dynamic technologies and processes can lead to inadvertent changes and exposures affecting your cloud security posture. FortifyData will monitor your cloud for misconfigurations and opportunities for hardening, and we provide actionable recommendations to continuously improve your cloud security posture.

Configurable Scoring Model
FortifyData’s patented configurable scoring model presents a direct indication of breach susceptibility that considers the likelihood of threat scenarios, asset classifications and risk impact to the organization. Clients can assign and modify weights attached to each cybersecurity risk category when calculating custom scores. This enables users to increase/decrease the relative impact of individual cybersecurity risks.
