- Platform
Platforms
- Solutions
- Industries
Industries
- Why FortifyData
Why FortifyData
"This is an excellent starting point for any organization that wants to get serious about their cyber risk management. The system has the capability to grow as you become more sophisticated in your use"
IT Director
Services Industry - Company
Company
- Partners
Partners
- Resources
Resources
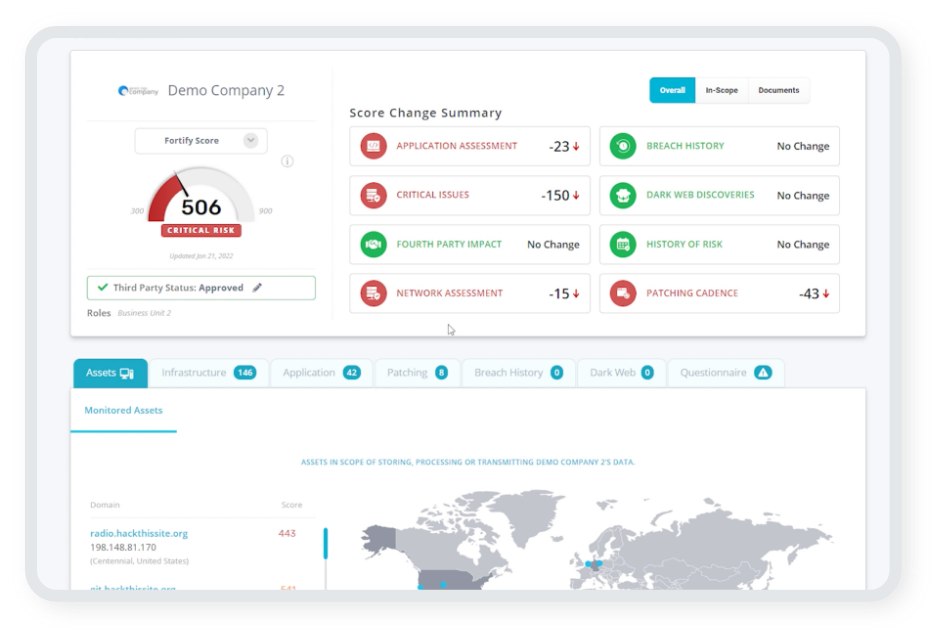
Get an Attacker's View of Your Business
Attack Surface
Management (ASM)
Attack Surface Management (ASM) identifies your company’s IT assets as an attacker will. FortifyData assesses all ports and services of an organization’s external and internal attack surface and identifies the same vulnerabilities an attacker would. Our platform discovers, identifies, and monitors your assets for vulnerabilities, and we prioritize findings based on the likelihood of data breach scenarios.
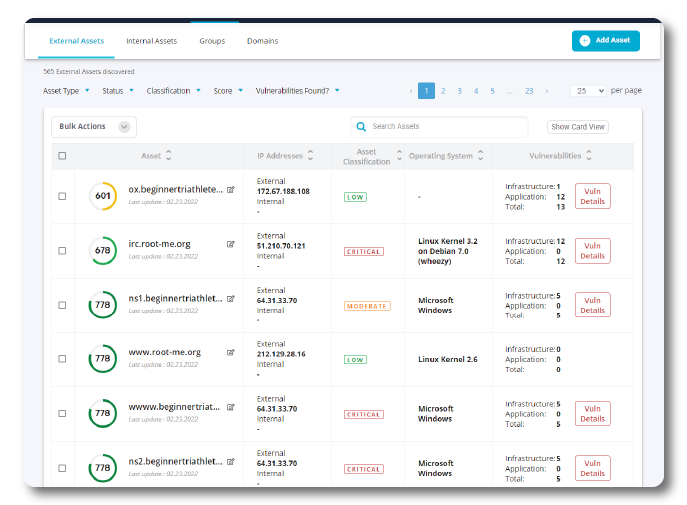
Identification & Classification of Assets
FortifyData automatically identifies your public facing assets and detects vulnerabilities across your attack surface to determine the most critical risks to your business.
Download our ASM Comparison Brief
See how FortifyData provides an accurate and comprehensive attack surface management solution.

Dynamic Attack Surface Protection
Continuous discovery and inventory are critical elements in your cyber resilience. Stay informed of the latest vulnerabilities present across your entire attack surface. Our data provides continuous insightful risk analysis related to shadow IT, cloud infrastructures, endpoint devices and your parties
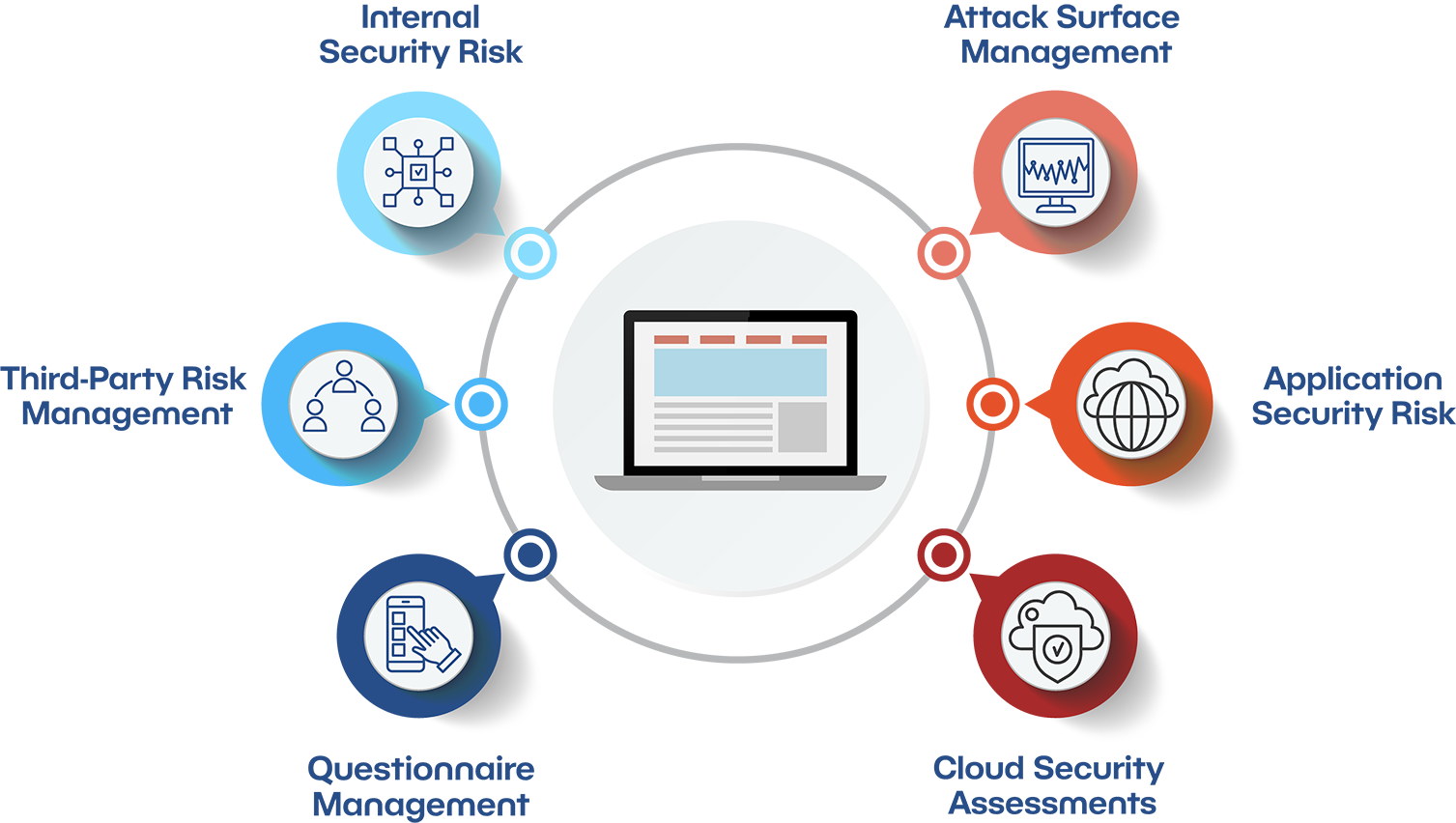
Internal Security Risk
Internal Security Risk
Stay vigilant for changes to your internal risk posture from unauthorized access, insider threat and misconfigurations. Learn how we provide timely visibility to internal risks at your organization..Learn More
Third-Party Risk Management
Third-Party Risk Management
Today’s interconnected supply chain means risks from third-parties affect your enterprise risk profile. Get live assessment data of the third-party vulnerabilities and threats that can affect you.Learn More
Questionnaire Management
Questionnaire Management
Keep up to date on the compliance of your suppliers with your program and their compliance against frameworks for your third-party program with auto-validated questionnaires leveraging the live assessment data of their environment.
Attack Surface Management
Attack Surface Management
Gain visibility of your known and unknown risks associated with external assets related to Shadow IT, remote/hybrid work and DevOps activities for effective cyber risk management. Get a hold on your attack surface.Learn More
Application Security Risk
Application Security Risk
Web applications and APIs have been identified as a leading source of cyber incidents. Learn how to manage your application security risk.Learn More
Cloud Security Assessments
Cloud Security Assessments
Dynamic technologies and processes can lead to inadvertent changes and exposures affecting your cloud security posture. Monitor your cloud for misconfigurations and opportunities for hardening.Learn More
Integrated Threat Intelligence Informs Your Risk Prioritization
The FortifyData platform integrates threat intelligence feeds that are updated hourly, so you get immediate prioritization of risks according to threats against the industry and technologies. Information such as the threat groups and trending threats like malware variants that are targeting the Higher Education industry.
- Our assessments identify your external assets susceptible to known threat activities such as malware
- With FortifyData’s internal agents we can identify if threat signatures are present on systems and in files
The threat intelligence feed data is integrated into our risk prioritization, so as threat intelligence changes – related to susceptible assets you have, increase in activity against the industry and threat signatures – the FortifyData platform analysis takes this into account for the threat likelihood calculation and adjusts your risk prioritization accordingly.
Ready to see the active threats?
Get in Touch
To learn more about how to protect your business from cyber risk, contact us directly.

