- Platform
Platforms
- Solutions
- Industries
Industries
- Why FortifyData
Why FortifyData
"This is an excellent starting point for any organization that wants to get serious about their cyber risk management. The system has the capability to grow as you become more sophisticated in your use"
IT Director
Services Industry - Company
Company
- Partners
Partners
- Resources
Resources
Cyber Risk Management for Technology Companies

Cyber risk is important for any organization, but especially those in the technology industry who are constantly innovating and expanding their digital footprint to meet customer demands and keep pace with the competition. Many security teams at these organizations are faced with managing the risk of a widely dispersed workforce, a continuously growing vendor ecosystem and global customers.
There are numerous compliance regulations these organizations must meet, like PCI-DSS, GDPR, SOC2, FedRAMP/NIST SP 800-53 plus more, depending on the audience they serve.
Manage Cyber Risk and Compliance in One Comprehensive Platform
FortifyData’s platform helps technology companies manage their cyber risk and regulatory compliance programs. FortifyData enables these organizations to continuously identify assets, view and manage risks across multiple locations, perform third-party risk management of vendors that may serve the entire organization or only specific departments. Also, manage the applicable regulatory compliance (PCI-DSS, GDPR, SOC2, etc.) and questionnaire processes. FortifyData takes all this into account and can also provide a security rating for the entire business or specific departments.
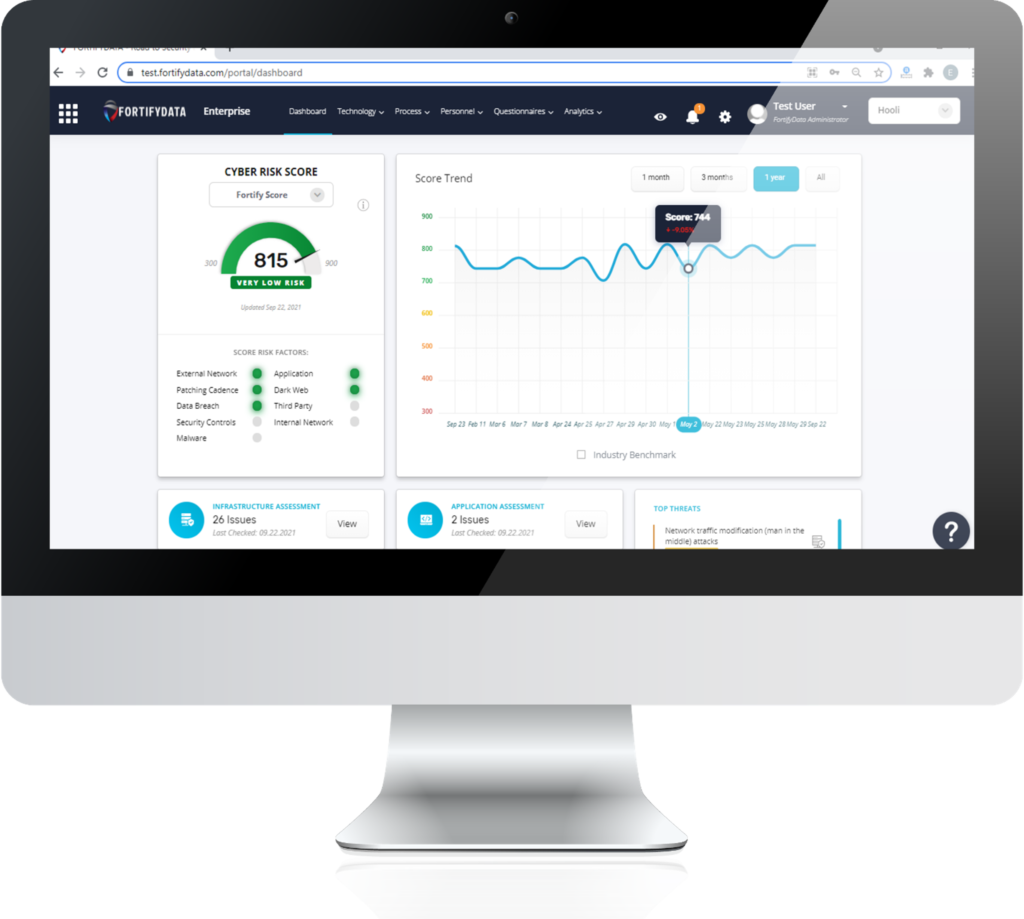
Why Technology Companies Choose FortifyData
- We work with a variety of technology, business services, cloud-based and tech-enabled service companies
- FortifyData provides a holistic view of cyber risk across the organization with the ability to drill down into specific departments or assets
- Prioritized view of risks with recommended remediation steps for identified vulnerabilities
- The accuracy of our risk assessment findings is based on continuous, direct, assessments of the technology company’s assets, services and processes that provide an up-to-date view of cyber risk
- Monitor cyber risk management progress compared to other technology companies
- FortifyData has been working with technology companies across the Nation to more accurately understand their cyber risk exposure of external, internal, cloud and third parties.
Solutions for Technology Companies

Attack Surface Management and Risk-based Vulnerability Management
Starting with asset discovery and inventory, our Attack Surface Management (ASM) identifies your technology organization’s IT assets as an attacker will. FortifyData assesses all ports and services of a company’s external and internal attack surface and identifies the same vulnerabilities an attacker would. Our vulnerability prioritization capabilities help you cut through the noise and get a view of the vulnerabilities with the most impact that actually matters; you can view this across the entire company or by specific department. You get a prioritized risk approach that considers context through asset classification, threat likelihood, and business impact, so you know where to focus time and resources on the most critical vulnerabilities to your organization.

Managing Compliance, Improving Reporting and Communication
FortifyData’s automated platform helps to streamline aspects of the compliance monitoring and reporting activities. The platform helps a technology company to meet certain requirements of various compliance frameworks (PCI-DSS, GDPR, SOC2, etc.) for cyber risk management, assessments, vulnerability management and third-party risk management.
Additionally, reporting from the FortifyData platform provides easy to understand reports with underlying detail to better report and communicate compliance management with stakeholders.
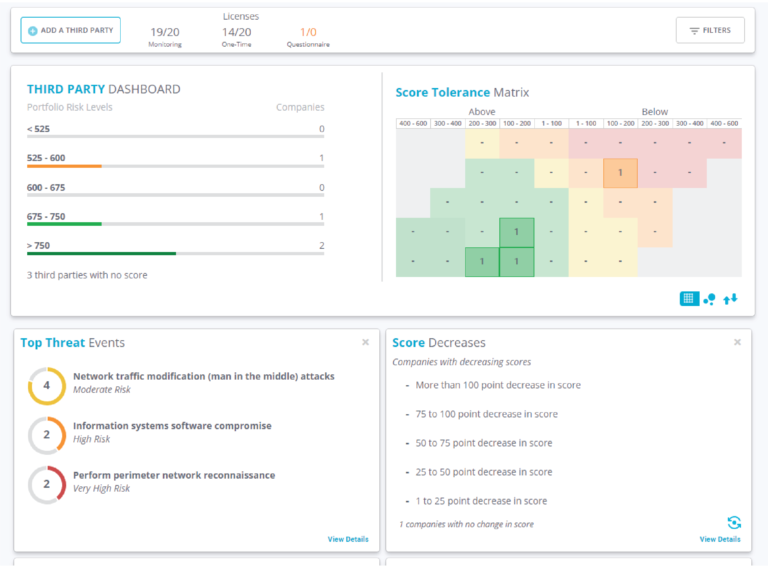
Third-Party Cyber Risk Management
Effectively evaluate a vendor and the specific service or product a vendor provides.
Technology companies often rely on software and services from other technology partners that are integrated to deliver a new service. Gain visibility into third-party cyber risks with continuous assessments of their external assets. We integrate our technology assessment findings to our embedded standard compliance or custom questionnaires to perform auto-validation that saves time in reviewing responses. Keep up to date on the compliance of your suppliers with your policies, and quickly identify vendors that do not comply. Get the full picture of external vulnerabilities at your third parties with our auto-validated questionnaires that leverage the live assessment data conducted on their environment. This provides you with the answers you need more quickly (in the time to run an assessment) than a manual questionnaire process. Create custom questionnaires that are specific to each vendor. Easily assign tasks and collaborate and track questionnaires with our task management capabilities.
Speed up vendor evaluations by spending less time reviewing questionnaires with FortifyData’s Questionnaire Exchange. Participants instantly access shared validated cyber risk assessments and questionnaires, allowing you to quickly make risk based decisions.



