- Platform
Platforms
- Solutions
- Industries
Industries
- Why FortifyData
Why FortifyData
"This is an excellent starting point for any organization that wants to get serious about their cyber risk management. The system has the capability to grow as you become more sophisticated in your use"
IT Director
Services Industry - Company
Company
- Partners
Partners
- Resources
Resources
FortifyInternal
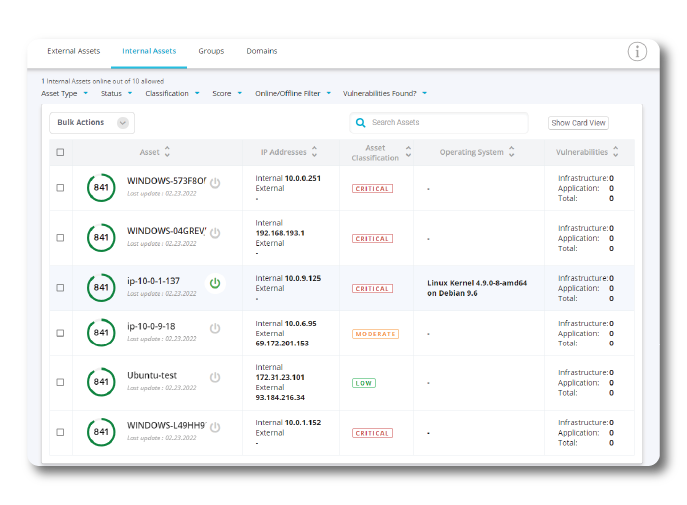
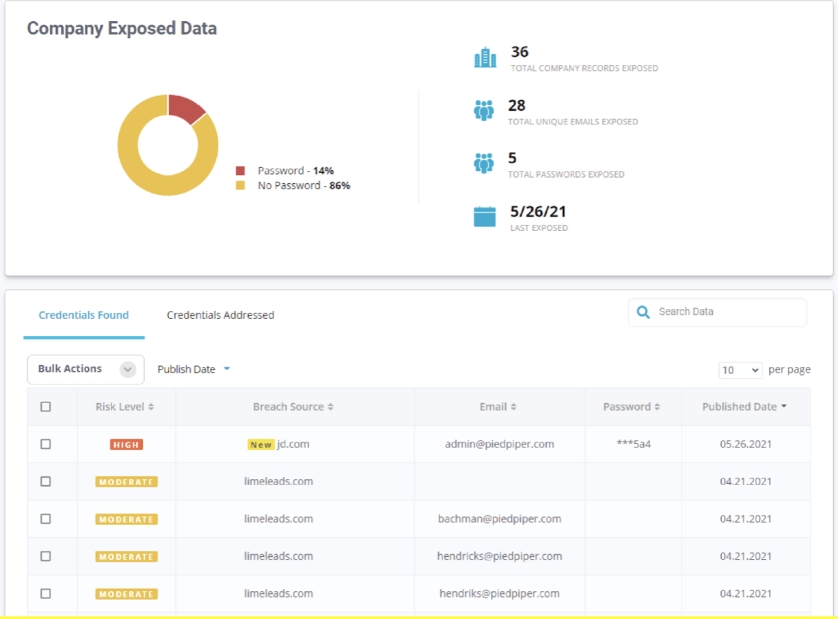
FortifyInternal is FotifyData’s Enterprise Cyber Risk Management solution that provides comprehensive visibility of your internal vulnerabilities and threats across your technology, people, processes and control effectiveness.
Comprehensive Risk Management
FortifyData uses non-intrusive active and passive assessments to uncover vulnerabilities of your internal environment with considerations to security controls implemented. Our platform allows you to ingest any type of risk or security data to build out a customizable risk scoring model. Having a view of your internal risks combined with your external risks enables better prioritization, triaging, and awareness.
All of the internal risk information is analyzed by the FortifyData platform and listed in a prioritized view based on vulnerability rating. The internal risk information is another component that factors into the security rating we produce for organizations so they can benchmark the security program progress and effectiveness. FortifyData enables organizations with full access to classify systems, adjust likelihood and impact of threats. This provides confidence and the most accurate view of cyber risk exposure to your key stakeholders, board and customers.