- Platform
Platforms
- Solutions
- Industries
Industries
- Why FortifyData
Why FortifyData
"This is an excellent starting point for any organization that wants to get serious about their cyber risk management. The system has the capability to grow as you become more sophisticated in your use"
IT Director
Services Industry - Company
Company
- Partners
Partners
- Resources
Resources
Cyber Threat Assessments

FortifyData cyber threat assessments are automated and continuous assessments of your organization giving you up to date findings on the latest vulnerabilities, threats and risks facing the attack surface of your organization, be it internal, external, cloud or third-party. FortifyData automates a lot of the steps and processes, incorporates templates and consolidates the cyber threat assessment tool capabilities you’ll read about below into one platform. Our assessments align with, and can supplement, annual threat assessments done by your team, external teams or consultants.
The FortifyData platform incorporates NIST Cyber Security Framework (CSF), NIST SP 800-53 and aligns with many other regulatory requirements for assessments, remediation and risk reporting. You will recognize their influence when it comes to assessing and analyzing the technological risks and vulnerabilities, calculating threat likelihood and risk adjustment criteria within the platform.
Looking to automate cyber threat assessments? FortifyData can help you.
Why Cyber Threat Assessments Are Important
Protecting your company requires you to continuously assess it for exploitable vulnerabilities from various threat vectors. This results in you, seeing how your organization is viewed by threat actors, hackers. You’ll need to have a plan to assess your external attack service, internal networks, human risks, cloud security posture and third-party vendors to get a comprehensive view. Then align this against policies and implement controls to mitigate and remediate the findings of the cyber threat assessments. What is a cyber threat assessment example that you can reference? We’ll provide details on cyber threat analysis tools, and how to conduct cyber threat assessments.
This is where a cyber threat assessment can guide you to identify the most critical vulnerabilities, how the threats and risks should be prioritized, best practices to fix them, enrich the analysis with cyber threat intelligence to inform you if threat groups are targeting you, company data is on the dark web or if any assets are compromised and controlled without your knowledge.
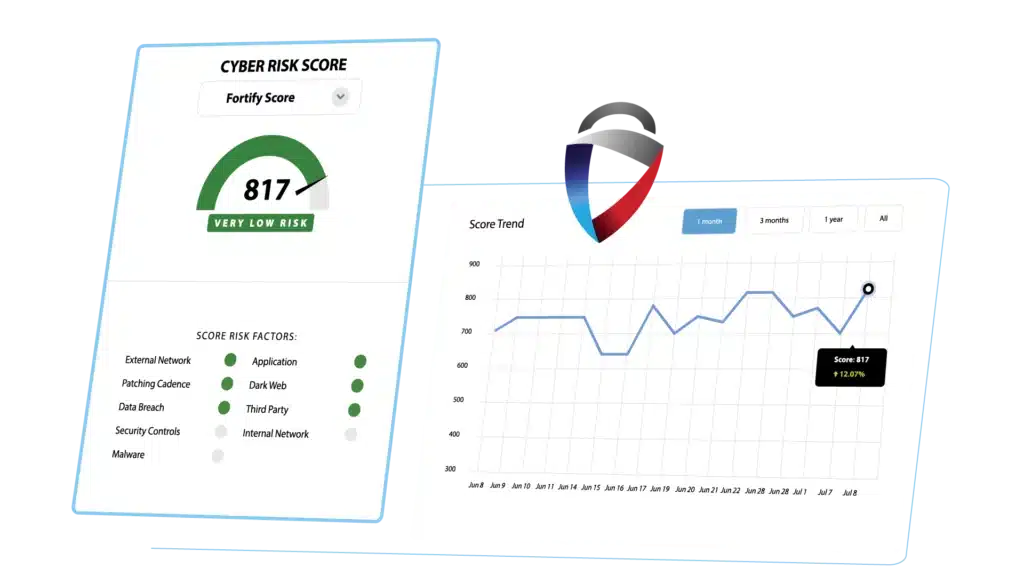
Source: FortifyData, Cyber Threat Assessment Dashboard
In today’s digital landscape, where data reigns supreme, ensuring its security is paramount. Yet, amidst the ever-evolving threats lurking in the cyber shadows, it can be challenging to know where to begin. Enter the cyber threat assessment, a vital tool in every organization’s cybersecurity program.
Cyber threat assessments play a pivotal role in safeguarding digital landscapes, offering a proactive approach to identifying and mitigating potential risks. In this comprehensive guide, we delve into the intricacies of cyber threat assessments, exploring examples, cyber threat analysis tools, and their overarching significance.
Before we delve into the nitty-gritty, let’s dispel a common misconception: cyber threat assessments aren’t just for tech giants or government agencies. Every organization, regardless of size or industry, possesses valuable data that attracts malicious actors. From mom-and-pop shops to Fortune 500 companies, understanding and mitigating cyber threats is a critical step towards securing your digital assets and there are processes and cyber threat assessment tools and services for any budget level that can get you started.
So, what is a cyber threat assessment, and why should it be on your priority list? This comprehensive guide will equip you with the knowledge and tools to navigate the complex world of cyber threats and ensure your organization’s resilience in the face of digital adversaries.
What is a Cyber Threat Assessment?
Cyber threat assessments are systematic processes that identify, analyze, and assess the potential threats your organization faces in the digital realm. They act as a roadmap, illuminating vulnerabilities, evaluating attacker motives and capabilities, and ultimately, informing data-driven decisions to bolster your cybersecurity posture. Add threat analysis tools to the cyber threat assessment and you start to benefit from automation and scalable tools to conduct your cyber threat assessment. Think of it as a security checkup for your digital infrastructure, highlighting potential weaknesses (vulnerabilities) in your cybersecurity posture before they can be exploited.
What is the Basic Cyber Risk Assessment?
Cyber threat assessments encompass a range of methodologies and tools. The range that a company can conduct a basic cyber risk assessment start at one end of the range in the form of a manual process that can reference a cyber risk assessment pdf to address fundamental elements to the other end of the range with a variety of cyber risk assessment tools and consultants to help operationalize a continuous plan. The key is to start a cyber threat assessment process and improve from there. Here are some key components:
- Vulnerability Identification: This involves pinpointing weaknesses in your systems, applications, and networks that could be exploited by attackers. Think of it as identifying holes in your digital fortress.
- Threat Intelligence Gathering: This involves gathering information about potential attackers, their tactics, and the latest cyber threats circulating in the online underworld. Knowing your enemy is half the battle.
- Risk Assessment: By analyzing the likelihood and impact of potential threats, you prioritize risks and allocate resources effectively. Not all threats are created equal, so understanding their severity is crucial.
- Reporting and Recommendations: The information gleaned from the assessment is meticulously documented, outlining vulnerabilities, risks, and actionable recommendations for mitigation. This is your blueprint for strengthening your defenses.
There are cyber risk assessment tools, like FortifyData, that can help you automate a lot of the cyber risk threat assessment process and continuously assess your company for proactive cyber defense.
What Are the Methods for Assessing Cyber Threats?
There are a couple of methods to assessing cyber threats to meet the cybersecurity risk assessment definition which ISACA defines as “assessments performed to allow organizations to assess, identify and modify their overall security posture and to enable security, operations, organizational management and other personnel to collaborate and view the entire organization from an attacker’s perspective.”
The best cyber threat assessment is the one that aligns with your specific needs. Choose from these options of cyber threat assessments examples:
Basic Cyber Risk Assessment: A high-level overview of your security posture, ideal for organizations just starting their cybersecurity journey.
Penetration Testing (Pen Testing): Simulating real-world attack scenarios to identify exploitable vulnerabilities and leverage the exploit to gain access to company systems for further advancement within a company network and systems. Think of it as a stress test for your defenses.
Vulnerability Assessment: A comprehensive scan of your systems (internal, external, cloud, etc.) for known vulnerabilities, providing a targeted list of assets that may need patching or other compensating controls to mitigate the risks.
Threat Modeling: Proactively identifying all potential threats and vulnerabilities that are at risk and the potential for exploitation, before they materialize. This is like pre-empting the enemy’s moves on a cybersecurity chessboard. Depending on where you read, there are between eight and thirteen different methodologies for threat modeling that security teams can follow. Some of the more commonly used ones are: STRIDE, PASTA, CVSS, Attack Trees, Security Cards, hTMM, Trike, VAST. Read more about these different threat modeling methodologies.
How to do a cyber threat assessment
Here are the fundamental steps for conducting a cyber threat assessment. Many organizations will do this in a manual approach with a cyber threat assessments template free, and also leverage a few cyber threat analysis tools, but imagine if this was automated. How much better would your time be spent if this was automated. Also consider that the outcome of your organization’s cyber threat and risk posture will benefit from a continuous and automated cyber threat assessment solution?
- Define Scope and Objectives: Clearly outline the areas to be assessed and the desired outcomes. Is this for a particular regulation or compliance requirement? For continuous awareness and visibility? This helps focus your efforts, identify the internal teams, asset administrative owners and/or service providers that may need to be involved to ensure a cost-effective assessment.
- Data Gathering: Compile information about your assets, systems, and network configurations. This can be from vulnerability assessments, penetration tests, DNS records, CMDB. Think of it as gathering intel about your own landscape.
- Vulnerability Identification: Employ scanning tools and threat intelligence sources to uncover weaknesses in your infrastructure. Review your patching cadence and specifically any exceptions the organization has made that require compensating controls or other safeguards to reduce the risk associated to IT assets, services or technology that were not patched regularly.
- Threat Modeling: Analyze potential attack scenarios and assess the likelihood and impact of each threat. This considers the steps above, your business context, industry, geo-political threats to develop threat models and what your organization will do about them.
- Risk Assessment: Prioritize identified risks based on their severity and likelihood. This should take into account your business impact analysis, which identifies your IT assets in order of operational critical priority (focus on the cyber threats and risks impacting your most critical systems) to produce the risk assessment with a risk-based view of vulnerabilities and threats to remediate and mitigate.
- Reporting and Recommendations: Document the findings and provide actionable recommendations for mitigating risks. This will be important for trending over time. What new assets or vulnerabilities appear? How have we been doing on patching cadence by agreed remediation timeframes? Can this be sent to stakeholders for an easy understanding of what the next steps are.
- Implementation and Monitoring: Take concrete steps to address identified vulnerabilities and continuously monitor your security posture.
For any organization this can seem overwhelming. With the threat landscape and IT environments changing so rapidly, the biggest benefit an organization can gain is to automate this process away from a cyber threat assessments pdf or cyber threat assessments template free. That is one of the reasons why FortifyData exists – to continuously identify, classify and monitor assets, automatically conduct analysis (which clients help inform) to produce a continuous view of recommendations to identified cyber threats and risks.
What are the Different types of cybersecurity threat assessments?
Beyond the basic cyber threat assessments, organizations delve into specialized cybersecurity assessments, and this can be driven by regulatory compliance. HIPAA or HITRUST for healthcare, NYDFS, GLBA, PCI DSS for financial services, ISO, SOC 2 and many others that are industry agnostic may have unique criteria or slightly differing requirements you can use in a cyber security risk assessment checklist. Your organization will need to determine which requirement of an assessment you’ll want to incorporate into your process. For companies that do business in multiple industries, you may have to conduct a cyber threat risk assessment with many different regulations that have some unique and some overlapping requirements.
Cyber Security Risk Assessment Checklist A cyber security risk assessment checklist adapts to different types of assessments, ensuring a comprehensive approach across various cybersecurity domains. We revisit some of the fundamental or basic cyber threat assessment criteria in the paragraphs above.
NIST Cyber Risk Assessment Aligning with industry standards, such as NIST, enhances the rigor and effectiveness of cyber risk assessments. Many of the common assessments for NIST are the NIST Cyber Security Framework (CSF), NIST SP 800-53, NIST SP 800-171. There are many NIST assessments including NIST’s own publications for doing a risk assessment – NIST SP 800-30 r1.
Aligning with industry standards, particularly the National Institute of Standards and Technology (NIST), significantly enhances the rigor and effectiveness of cyber risk assessments. NIST cyber risk assessment:
- NIST Cybersecurity Framework Assessment Organizations aligning with the NIST Cybersecurity Framework gain a structured approach to assessing and improving their cybersecurity posture. This framework provides a comprehensive set of guidelines and best practices, ensuring a systematic evaluation of cybersecurity risk.
- Security Control Assessments (SCA) Following NIST guidelines, Security Control Assessments evaluate the effectiveness of security controls within an information system. This process ensures that controls are implemented correctly and operate as intended, minimizing the risk of cyber threats.
- Continuous Monitoring Assessments NIST emphasizes continuous monitoring as a key component of effective cybersecurity. Assessing security measures continuously ensures that organizations remain vigilant against evolving cyber threats, enabling prompt responses to emerging risks.
Advanced Persistent Threat (APT) Assessments In the realm of cybersecurity, APT assessments focus on identifying and mitigating prolonged and targeted cyber threats. This assessment goes beyond routine checks, delving deep into understanding the tactics, techniques, and procedures (TTPs) employed by persistent adversaries.
Vulnerability Assessments To fortify defenses, organizations conduct vulnerability assessments to pinpoint weaknesses within their systems. These assessments provide insights into potential entry points for cyber threats, allowing proactive patching and reinforcement.
Penetration Testing Going beyond theoretical assessments and vulnerability assessments, penetration testing involves simulated cyberattacks to evaluate the resilience of an organization’s defenses. By emulating real-world scenarios, this assessment builds on the identified vulnerabilities of a vulnerability assessment and gauges the effectiveness of security measures.
Compliance Assessments Organizations operating in regulated industries must adhere to specific compliance standards. A cyber security risk assessment checklist, tailored to compliance requirements, helps ensure that the organization meets the necessary regulatory frameworks.
Incident Response Assessments Preparing for and responding to cyber incidents is a critical aspect of cybersecurity. A cyber security risk assessment checklist, when applied to incident response planning, ensures a well-coordinated and efficient reaction to potential security breaches.
Cloud Security Assessments As cloud adoption becomes ubiquitous, evaluating the security posture of cloud environments is paramount. The checklist, when applied to cloud security assessments, helps organizations identify and address vulnerabilities unique to cloud infrastructures.
Incorporating these additional cybersecurity assessments into an organization’s strategy augments the overall resilience against a diverse range of cyber threats. By combining comprehensive cyber security risk assessment checklists, advanced assessments, and aligning with industry standards such as NIST, organizations can establish a proactive and adaptive approach to cybersecurity.
What is a threat assessment template?
Threat assessment templates are crucial in helping to identify cyber threats and cyber risks to develop an effective cyber risk management program. There are a few different cyber threat assessment templates to consider – a simple cybersecurity risk assessment template, information security risk assessment template, cybersecurity risk assessment report template, cybersecurity risk assessment checklist, cyber risk mitigation plan matrix. Many of these are excel or spreadsheet based cyber threat assessment templates thus making them a manual process (maybe they have some excel macros to run, but you get the idea). Reach out if you want to discuss how we automate this process.
Cyber Threat Analysis Tools Your cyber threat assessment, cyber risk assessment, will need cyber threat analysis tools as part of the process. Whether your own tools, those of a consultant/advisor/auditor, will need a variety of tools to help. These cyber threat analysis tools can include:
- Vulnerability scanners
- External attack surface monitoring
- Internal network monitoring
- Cyber threat intelligence feeds
- SIEM / logging tools
- Multi-factor authentication tool
- Cloud security configurations / logs
- Firewalls
- Email filters / Phishing results
What is a Cyber Threat Assessment Example Examining real-world examples illustrates how threat assessment templates can be customized for diverse scenarios. Here are a couple of cyber threat assessment examples:

Source: Smartsheet.com – cyber security risk assessment template examples
martsheet has many templates available, for those that are seeking a spreadsheet for manual risk assessments. Save time, reduce errors, reduce human dependency, and make your cyber risk assessments continuous and talk to FortifyData about automating your cyber risk assessments.
What is a Cyber Threat Assessment PDF Delving into the specifics of cyber threat assessments in PDF format, highlighting their role in threat assessment templates. NIST, through NISTIR 8286A – Identifying and Estimating Cybersecurity Risk for Enterprise Risk Management, provides an excellent cyber threat assessment PDF for organizations to reference in identifying cyber risks and threats.
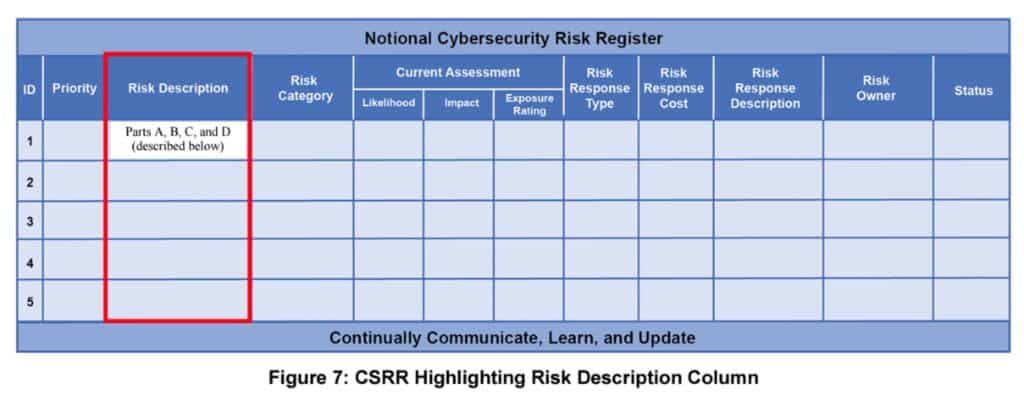
Source: NIST.gov, NISTIR 8286A – Identifying and Estimating Cybersecurity Risk for Enterprise Risk Management
What are the steps in cyber threat assessment?
Now, let’s navigate the practicalities of conducting a cyber threat assessment. Think of this as the start of a cyber security risk assessment checklist and each of these domains of the assessment will have more defined requirements and recommendations that comprise a subsequent checklist of actions that go into a cyber threat assessment:
Define Scope and Objectives: Clearly outline the areas to be assessed and the desired outcomes. This helps focus your efforts and ensures a cost-effective assessment.
Data Gathering: Compile information about your assets, systems, and network configurations. Think of it as gathering intel about your own landscape.
Vulnerability Identification: Employ scanning tools and threat intelligence sources to uncover weaknesses in your infrastructure.
Threat Modeling: Analyze potential attack scenarios and assess the likelihood and impact of each threat.
Risk Assessment: Prioritize identified risks based on their severity and likelihood.
Reporting and Recommendations: Document the findings and provide actionable recommendations for mitigating risks.
Implementation and Monitoring: Take concrete steps to address identified vulnerabilities and continuously monitor your security posture.
What is a cyber threat assessment pdf that incorporates all these steps and findings? The FortifyData platform has reporting capabilities that can produce your cyber threat assessment pdf for sharing with stakeholders. There are various levels of detail of data to be shared from a simple executive summary to a full vulnerability listing that can be produced as a cyber threat assessment pdf.
Many security leaders and practitioners seek a cyber threat assessment template free to analyze these aspects. Platforms like FortifyData offer some scalable advantages in that the identified domains and the underlying steps and requirements are built into the platform making the cyber threat assessment more automated with reporting and review of each of these sections reviewable and auditable. If you want to see how well your company fares in a cyber threat assessment template free assessment FortifyData can provide that initial assessment.
What are the Methods of Threat Analysis?
Effective threat analysis involves the study of how an attacker will use identified vulnerabilities to gain access to the organization to access sensitive data or IT assets and systems. Some of the methods of threat analysis include:
- Data breaches: Unauthorized access or theft of sensitive information.
- Malware attacks: Software designed to harm systems or steal data.
- Ransomware: Malicious software that encrypts data and demands payment for decryption.
- Denial-of-service (DoS) attacks: Overwhelming systems with traffic to render them unavailable.
- Social engineering attacks: Tricking users into revealing sensitive information or granting access to systems.
This is an evaluation of protocols, processes and procedures implemented to protect IT assets and services at an organization. Your analysis may determine that additional protocols and controls to mitigate the likelihood of threat scenarios occurring are needed. This can combine your threat modeling (see above) and risk assessment findings, or vulnerability findings, to study the potential exploitable vulnerabilities for threat vectors analysis.
Threat Analysis Tools help in identifying the vulnerabilities within your organizations IT networks and services. These are usually done on a defined interval, largely in accordance with company cybersecurity policies and/or compliance requirements. Additionally, services that add context – such as cyber threat intelligence feeds – help enrich your threat analysis with known exploitable vulnerabilities (KEV), common vulnerability and exposure (CVE) found withing your inventory of specific IT or cloud assets by threat groups.
There are cyber threat analysis tools, like FortifyData, that can help you automate a lot of the cyber risk threat assessment process and continuously assess your company for proactive cyber defense.
Examples of the types of threat analysis tools are:
- Vulnerability scanners
- External attack surface monitoring
- Internal network monitoring
- Cyber threat intelligence feeds
- SIEM / logging tools
- Multi-factor authentication tool
- Cloud security configurations / logs
- Firewalls
- Email filters / Phishing results
What is a Cyber Threat Assessment Example Real-world examples serve as valuable case studies, demonstrating how threat analysis methodologies have been applied successfully. What is a cyber threat assessment example references scenarios like these:
- Cyber-attack on an organization’s IT assets, systems, data or services (e.g., ransomware campaigns)
- Human errors from negligence or non-compliant behaviors (e.g., poor password use, clicking links)
- System failures of IT security controls (e.g., hardware, software)
- Natural disasters (e.g., earthquakes, floods)
What is the purpose of risk and vulnerability assessments?
Vulnerability assessments are to identify known vulnerabilities within your IT environment assets, systems and services. Companies are moving towards continuous vulnerability assessments due to the rapidly changing IT environment and threat landscape. It is becoming riskier to do vulnerability assessments on a quarterly or longer cadence; this is becoming known as continuous threat exposure management.
The risk assessment evaluates the overall vulnerabilities and threat scenarios that face your organization, assessing the likelihood and impact of threats should they occur, plan mitigations and remediations to improve your cybersecurity posture, understand where compliance and regulatory compliants influence or mandate policy, processes and controls and work towards continuous improvement to mitigate cyber risk to an acceptable level for your organization.
There are many cyber risk assessment tools, like FortifyData, that can help your organization conduct a thorough cyber risk assessment (a lot of which can be automated), which can include vulnerability assessments, you can achieve several key objectives:
- Understand Your Cybersecurity Posture: Analyze your systems, networks, and applications to identify vulnerabilities that attackers could exploit.
- Prioritize Risks: Evaluate the likelihood and impact of different threats to focus your resources on the most critical issues.
- Make Informed Decisions: Use the insights from the analysis to inform your cybersecurity investments, policies, and procedures.
- Proactively Mitigate Threats: Implement controls and countermeasures to reduce the likelihood or impact of cyberattacks.
- Improve Your Response Plan: Develop a plan for responding to incidents should they occur, minimizing downtime and damage.
Ultimately, the goal of cybersecurity risk assessment is to shift your cybersecurity strategy from reactive to proactive. One aspect many organizations should consider is to automate this process with a platform or integrated solution and reduce any manual processes associated with managing this with a cyber security assessment pdf. By understanding potential threats, you can prevent them from causing harm and ensure the security of your data and systems. The more you automate this process, you make the process more efficient and reduce human error and dependencies.
What is threat analysis tool?
A threat analysis tools, like FortifyData, are software applications or platforms designed to assist in identifying, assessing, and mitigating potential security threats to your organization’s assets. These tools can be invaluable in protecting your systems, data, and operations from cyberattacks, data breaches, and other malicious activities.
Here are some of the key features and functionalities that threat analysis tools typically offer:
- Vulnerability scanning: These tools can scan your systems and networks for known vulnerabilities, such as outdated software, misconfigured settings, and weak passwords.
- Threat intelligence gathering: They can collect and analyze data on emerging threats, attacker tactics, and industry trends to help you understand the current threat landscape.
- Risk assessment: They can help you assess the likelihood and impact of potential threats, allowing you to prioritize your security efforts.
- Reporting and visualization: They can generate reports and dashboards that summarize your findings and provide actionable insights.
- Integration with other security tools: They can integrate with other security tools, such as firewalls and intrusion detection systems, to provide a more comprehensive view of your security posture.
Here are some cyber threat analysis tools available:
- Crowdstrike Falcon Insight
- FortifyData Cyber Threat Assessment Platform
- Palo Alto Networks Cortex XDR
- Qualys VMDR
- Rapid7 InsightVM
- Trellix/McAfee ePO
The best threat analysis tools for your organization will depend on your specific needs and budget. However, some factors to consider when choosing a tool include:
- The size and complexity of your IT infrastructure
- Your industry and regulatory compliance requirements
- Your budget
- The level of expertise of your security team
By using a cyber threat analysis tool, you can gain valuable insights into your security posture and take proactive steps to mitigate potential risks. This can help you protect your organization from cyberattacks and ensure the security of your data and systems.
