A security rating (also referred to as a cybersecurity risk rating) is a quantifiable metric that communicates an organization’s or third-party’s cyber risk posture over time. Security ratings calculations initially focus on the external security posture of an organization based on passive assessment and data collection about the company’s assets and internet presence, in addition to active assessments. A security rating is used for an ‘at-a-glance’ analysis of the cyber risk that an enterprise or vendor has over a period of time.
A security rating can also consider internal, cloud and third-party risks and vulnerabilities to arrive at an overall security rating. This helps security leaders to understand the progress of their security program and the effectiveness of controls in place which helps them manage the program.
Many security rating services start with assessments of the external security posture for an organization that provides an ‘outside’ or ‘attacker’s view’ of the organization. Clients working with a security rating provider can incorporate the internal, cloud and third-party risks to get a more comprehensive and contextualized security rating
A security ratings vendor provides an independent score and security rating on organizations. First-generation security rating services vendors like BitSight or SecurityScorecard provided point-in-time security ratings. Alternatives to BitSight and SecurityScorecard, as well as those companies, work to use updated technologies and methodologies to assess the cyber risk of organizations to provide more up-to-date security ratings.
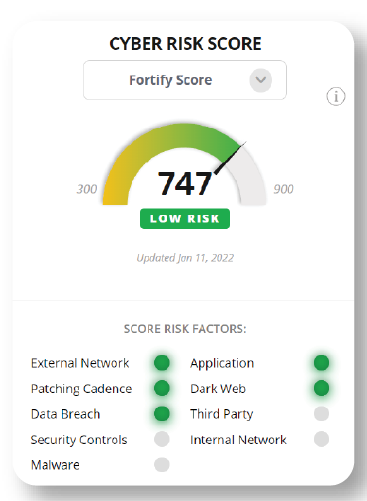
Each security rating services provider has their own methodology for the factors, weightings and calculations that produce a score. There is no standard in the security ratings industry, but there is a set of principles agreed to as outlined by the US Chamber of Commerce.
Many providers do not make their security rating methodologies available, so how are security ratings created? FortifyData has made their security rating score methodology publicly available and is the only security rating provider with a patent pending on their configurable security rating risk rating models. Providing adjustable security ratings allows clients to create additional security rating models, in addition to the standard FortifyData score, focused on the factors and weightings of those factors in the score that best address the organization’s specific threat landscape.

FortifyData bases our cyber security rating on the following characteristics:
Different security rating services providers have distinct security rating scales and methodologies. A security rating scale is a standardized metric used by cybersecurity rating providers to assess and communicate an organization’s cybersecurity risk posture. The scale typically ranges from numerical values (like a credit score) or alphabetic grades, with higher scores or grades indicating better cybersecurity practices and lower risk. The purpose of these scales is to provide a clear, objective, and consistent way to evaluate and compare the cybersecurity health of different entities where you can monitor their ratings trend over time- and compare to industry benchmarks.
“Good” security ratings generally want to be at the top of the range for the respective scales. That could be 650-900 for credit score style, 90-100 or 900-1,000 for numeric scales and A or B in the letter scales. Each security rating provider may have a different scale or provide both, but they all have the same intent- the higher the security rating, the less risk in an organization’s security posture.
How should organizations be using security ratings? In addition to getting an ‘at-a-glance’ analysis of an organizations cyber risk posture as a data point for enterprise risk management, a security rating can be used for additional methods:
Security ratings services provide cybersecurity leaders with the tools and insights they need to enhance their organization’s security posture, reduce cyber risks, and communicate effectively with stakeholders. These services offer a proactive and data-driven approach to cybersecurity management in an ever-evolving threat landscape.
For many security rating services providers it is impossible for a client organization to accept the risk to quickly affect their security rating. How do you:
Luckily, FortifyData enables clients to account for all of those that will more accurately portray the cyber risks the organization faces and their security posture for external, internal and cloud risks and vulnerabilities. FortifyData enables clients to classify identified assets by operational criticality (also allowing for identification of data types on devices) and respond to risks identified by recording the compensating control(s) in place to reduce the likelihood of threats occurring. This produces the most accurate security rating risk representation by the published security rating score.

Security ratings is a tracked industry by leading independent analyst organizations, like Forrester, Gartner and a few others. Most of what can be found is from 2019 with periodic updates since then. We anticipate updates from the various analyst firms on their previous research in the next 12 months.
Gartner has identified security ratings services as a component of third-party risk management according to Top 10 Security Projects for 2019. Largely the result of more interdependent relationships among companies, security ratings services can be an informative tool to help understand the external risk – absent any vendor provided infomration about internal security controls and effectiveness – to help inform supplier relationship decisions.
Forrester continues to evaluate security ratings services in a research cadence of every few years. According to Forrester’s publicly available evaluative research calendar, they are preparing to publish an update on Cybersecurity Ratings Services to their originally published Forrester New Wave: Cybersecurity Risk Ratings Platforms Q1 2021.
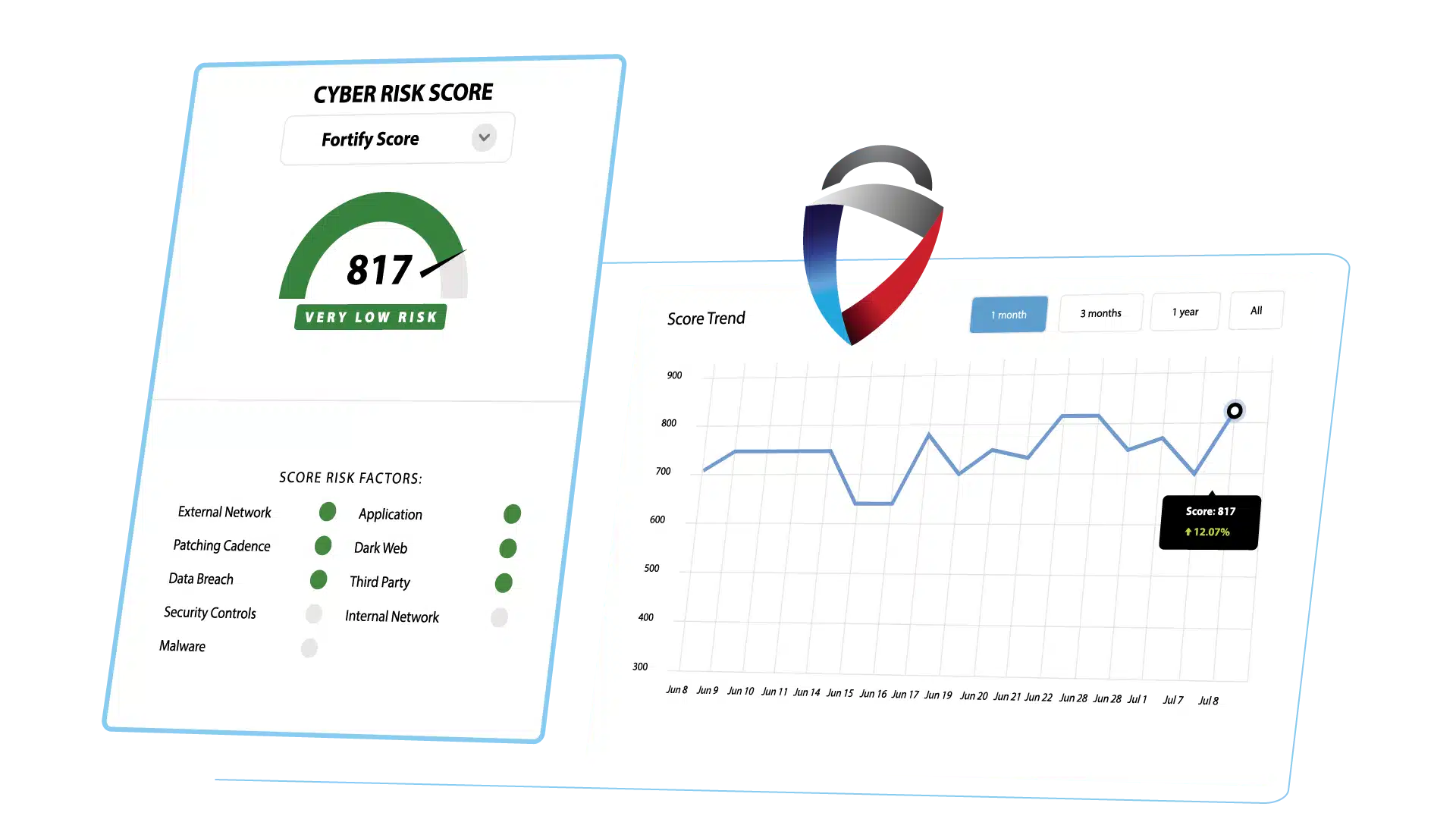
Security ratings are based on assessments of publicly available and/or external IT asset data. As associated vulnerabilities are remediated – and the security rating provider can detect the mitigation or remediation – the security rating will change. The change will incorporate any identified remediations/mitigations in addition to any new vulnerabilities or cyber risks it has detected based on their security rating methodology.
Some security ratings providers will not be able to detect all your specific changes as they may not be able to derive an accurate inventory of your external IT assets or based on the publicly available information they can acquire. Likewise, if a security ratings organization inaccurately identifies assets that are not yours, there may be little you can do. You do have the option to flag the asset for removal from your profile or the asset vulnerabilities may get remediated by the organization that owns it. That example can cause lots of frustration if the time to remove the asset is longer than what the improved rating is needed for (e.g., cyber insurance assessment).
FortifyData’s security rating is recalculated on a weekly basis, based on continuous assessments of an organization’s external IT. The FortifyData methodology confirms asset ownership which greatly reduces misattribution and false positives.
The first step towards improvement is understanding. A security rating is a metric that gauges an organization’s cybersecurity health. Below is an overview of examples of actions to take from improvements. You can read a full description on examples to improve your security rating and some suggestions to work with a security rating provider that publishes an inaccurate security rating on your organization
Addressing findings from assessments, educating your team and collaborating with third parties can help reduce and prevent attack surface exposures to result in an improved security rating. With a proactive approach, regular assessments, and a commitment to continuous improvement, any organization can enhance its security rating.
FortifyData provides a trusted and accurate security rating based on weekly external attack surface assessments of your confirmed IT asset inventory. We take into account asset classification, likelihood adjustments and compensating controls and enrich the findings with dark web discoveries and cyber threat intelligence to give you a contextualized security rating.
FortifyData is an industry-leading Continuous Threat Exposure Management (CTEM) company that enables the enterprise to manage cyber risk across the organization. By combining automated attack surface assessments with asset classification, risk-based vulnerability management, security ratings and third-party risk management, you get an all-in-one cyber risk management platform.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |