- Platform
Platforms
- Solutions
- Industries
Industries
- Why FortifyData
Why FortifyData
"This is an excellent starting point for any organization that wants to get serious about their cyber risk management. The system has the capability to grow as you become more sophisticated in your use"
IT Director
Services Industry - Company
Company
- Partners
Partners
- Resources
Resources
Threat Exposure Management Solution
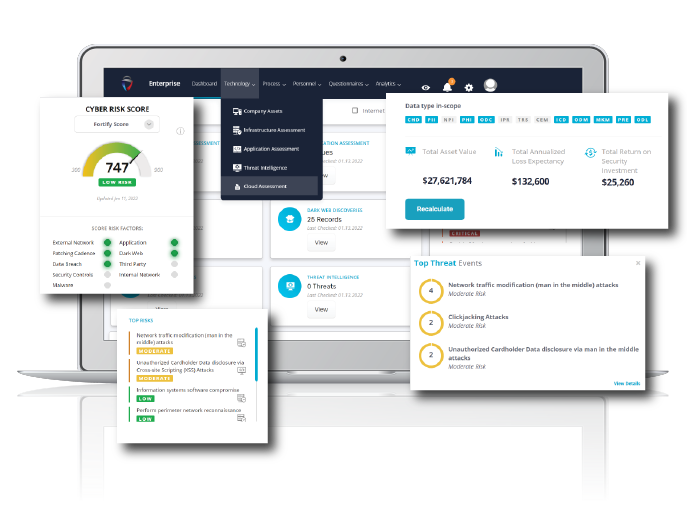
FortifyData’s platform identifies and manages threat exposures, and associated risks, across the entire attack surface. This approach helps you better manage cyber risk and threats by integrating asset and vulnerability management, integrates threat intelligence and produces a risk-based vulnerability view for the organization. Distilling all this down to a continuously updated security rating provides a view of your progress with threat exposure management at a “quick glance” that is shareable with additional stakeholders and with granular data you can dive deep on when you want to investigate further.
"One of biggest reasons we chose FortifyData is the ability to do fresh scans each week for our enterprise and each month for our third parties, and the scans are not based on any legacy data. That gives me a more accurate representation of what the security vulnerabilities are."
Director of Cybersecurity Services, U.S. Mortgage Lending Company
Why FortifyData for Threat Exposure Management?
The FortifyData platform was built to provide an integrated view of cybersecurity risks and threat exposures across external networks, internal networks, cloud misconfigurations and third-party exposures. The platform conducts direct assessments and uses machine learning algorithms to analyze live data against thousands of unique data points, using qualitative and quantitative risk assessment methodologies, giving organizations an integrated view of the cyber risk factors across an organization’s entire threat landscape along with actionable guidance to improve the organization’s risk posture.
Starting with attack surface assessments and leveraging asset classification to identify the value of assets to your business, provides an asset centric approach to risk management. FortifyData then integrates threat intelligence to give you a risk-based vulnerability management program to focus on the vulnerabilities with the most impact to your organization.

Attack Surface Management (ASM)
Continuous, direct, assessments of your attack surface. External assets, internal networks, cloud, third parties. Covering all ports and all services, this provides the most accurate view of assets and associated vulnerabilities.
Risk Based Vulnerability Management (RBVM)
Prioritized risk and remediation that is informed with threat intelligence and based on asset classification. See the threats and vulnerabilities that can negatively impact your business the most.
Third-Party Risk Management (TPRM)
Directly assess a third-party’s external attack surface, continuously or one-time, to verify the threat exposure that vendor poses to you. Save time with our Questionnaire Exchange to send and share questionnaires (standard or custom) with vendors and interested parties.

Security Ratings
Measure exposure management based on weekly assessments. FortifyData’s patented configurable scoring model presents a direct indication of breach susceptibility that considers the likelihood of threat scenarios, asset classifications and risk impact to the organization.
View and Manage Cyber Risk by Subsidiary, Department, or Business Unit
Get a unified view of cyber risk across the Enterprise with the ability to drill down and manage the risks within specific business units. Perfect for multi-national conglomerates, holding companies and university systems. For your third-parties, perform risk management of vendors that serve the entire Enterprise or only specific subsidiaries.
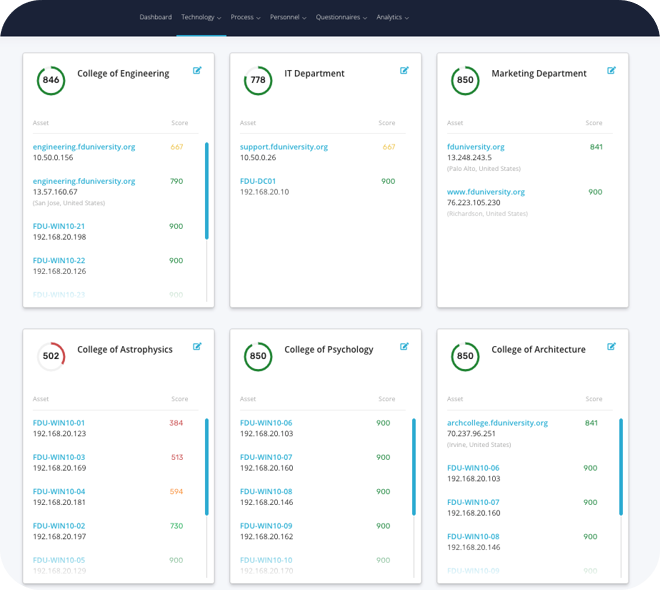
Why Enterprises Choose FortifyData
- Enterprise roll up; subsidiary management – Enterprises can continuously identify assets, view and manage risks by specific subsidiaries or business units. Perform third party risk management of vendors that serve the entire Enterprise or only specific subsidiaries.
- Tool consolidation; breakdown data silos – reduce costs and move to a solution that provides a unified view with more accurate data and no interoperability issues
- Continuous management – conducting continuous assessments results in a continuously updated view of prioritized risk and vigilant monitoring of attack surface
- Implementing feedback – we consistently meet with customers to understand how we can improve the platform to best meet their needs in managing rapidly changing risk
- Customer service – Our customer success team consistently receives high praise for being proactive with customer enablement, and is attentive and responsive to needs and requests



