Threat Groups Actively Targeting Higher Education Institutions
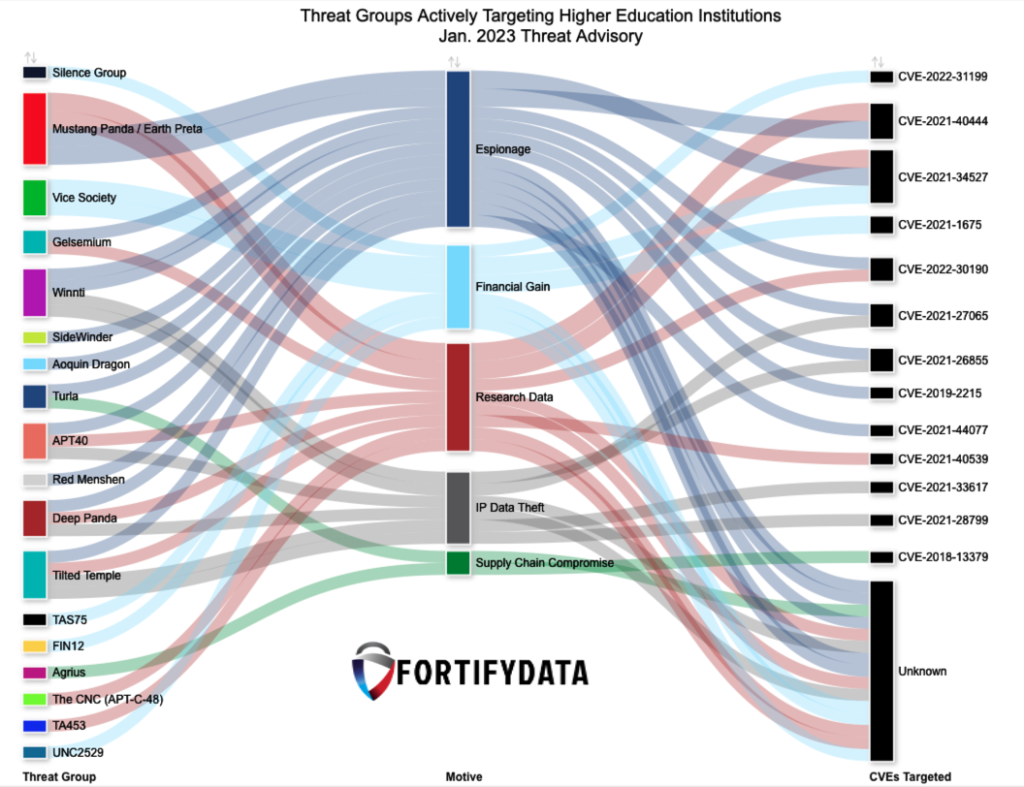
Threat Groups Actively Targeting Higher Education Institutions Jan. 2023 Threat Advisory Summary Threat intelligence can provide valuable insights into the latest vulnerabilities being actively exploited by cybercriminals, as well as the potential impact these vulnerabilities could have on your organization. This information can help you prioritize vulnerabilities and determine the most effective patching or mitigation […]
Threat Advisory: Chromium Zero Day (MS Edge and Google Chrome)

Threat Advisory: Chromium Zero Day(MS Edge and Google Chrome) Threat Chromium Zero Day (MS Edge and Google Chrome) Vulnerability CVE-2022-22941 CVSS – 8.8 HIGH Vulnerability Publication Date – 07/07/2022 Exploits Available – Yes, private Description There is very little information available about this vulnerability other than it has been exploited in the wild. Both […]
Threat Advisory: ISC BIND 9.18.0 < 9.18.3 Assertion Failure (CVE-2022-1183)

Threat Advisory: ISC BIND 9.18.0
Threat Advisory: Remote Procedure Call Runtime Remote Code Execution Vulnerability (CVE-2022-26809)

Threat Remote Code Execution through Microsoft RPC Vulnerability Remote Procedure Call Runtime Remote Code Execution Vulnerability (CVE-2022-26809)1 CVSS – 9.8 CRITICAL Vulnerability Publication Date – 4/12/2022 Exploits Available – Most Likely Description Of the 128 vulnerabilities in Microsoft’s April patch, 10 have a critical severity but CVE-2022-26809 is raising the most concern. The vulnerability […]
Threat Advisory: Spring Framework Spring4Shell Vulnerability (CVE-2022-22965)

Threat Remote Code Execution (RCE) in the Java Spring Framework Vulnerability Spring Framework Spring4Shell (CVE-2022-22965)1 CVSS – 9.8 CRITICAL Vulnerability Publication Date – 3/31/2022 Exploits Available Description The Spring4Shell Remote Code Execution vulnerability affects Apache Tomcat servers running JDK9+ with Spring library versions prior to 5.2.20 or 5.3.x prior to 5.3.18. After 26 years of […]
Cyber Advisory: Heightened Awareness Related to Russian Cyberattacks

Cyber Advisory: Heightened Awareness Related to Russian Cyberattacks As the Russian invasion of Ukraine progresses, having a heightened awareness for the potential cyber activities associated to the spillover of Russian cyberattacks is necessary. Whether it is spillover effects from the cyberattacks in Eastern Europe or specific targeting of industries attributed to Russia, these pose risks to […]
How to Identify and Mitigate Risks Associated with Log4j Vulnerability

How to Identify and Mitigate Risks Associated with the Log4j Vulnerability Most people know by now about the critical vulnerability in Log4j. The risk of this vulnerability is the ability for remote attackers to run arbitrary code on any application that uses Log4j, and it is already being actively exploited. You can find additional information and resources about the vulnerability […]
