- Platform
Platforms
- Solutions
- Industries
Industries
- Why FortifyData
Why FortifyData
"This is an excellent starting point for any organization that wants to get serious about their cyber risk management. The system has the capability to grow as you become more sophisticated in your use"
IT Director
Services Industry - Company
Company
- Partners
Partners
- Resources
Resources
Enterprise Cyber Risk Management
360° Risk Insight
Most rating providers are limited with only assessing the external attack surface of organizations with outdated open-source data, which is a dangerous practice that leads to a false sense of security. FortifyData uses non-intrusive active and passive assessments to uncover vulnerabilities of both your external and internal infrastructure with considerations to security controls implemented.
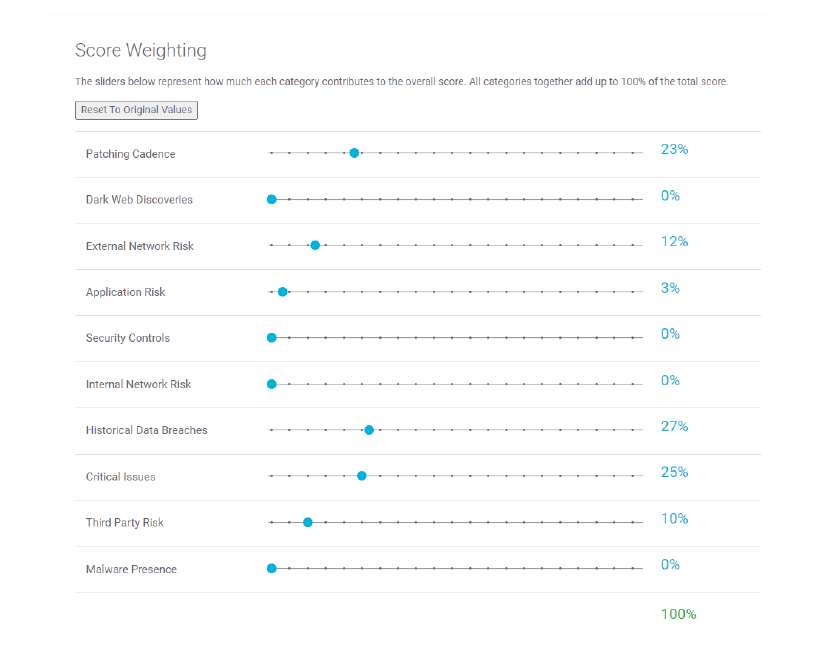
Manage Your Rating
To understand your risk exposure level, accuracy is everything. Fully manage your cyber risk rating and the factors affecting your risk profile using FortifyData, ensuring your risk rating is accurate—free of misattributions and false positives.
FortifyData’s comprehensive approach goes beyond traditional rating methodologies and gives you the flexibility to manage your security ratings with full access to classify your systems, adjust likelihood and impact of threats.
This enables you to confidently present the most accurate view of your cyber risk exposure to your key stakeholders, board and customers.

Custom Data Feed Integration
The FortifyData platform allows you to ingest any type of risk-informed data to build out a customizable scoring model. Examples below are solution data feeds that can be ingested and factored into a customized risk model:
• GRC platforms
• Vulnerability scanners
• SIEMs
• IDS/IPSs, and more.
Why FortifyData for Enterprise Risk Management?

Accurate Auto-Asset Discovery
Reduce asset misattributions with FortifyData’s auto asset discovery capability. While other solutions can take up to 4 months to update new asset inventory, we continuously search and identify new assets on a weekly basis.

Data Accuracy
FortifyData collects data through both active and passive assessment methodologies, not relying on historical, OSINT data. We continuously reassess to make sure all attack surface data is timely and accurate.

Continuous Infrastructure Security Assessments
Reduce asset misattributions with FortifyData’s auto asset discovery capability. While other solutions can take up to 4 months to update new asset inventory, we continuously search and identify new assets on a weekly basis.
Dark Web Intelligence
Our proprietary intelligence feeds alert clients when data has been compromised, either within your organization or through a thirdparty entity. Through continuous dark/deep web scanning of files and databases across social media, un-indexed and transient deep websites, we will alert you of exposed company records, including leaked information, stolen credentials and confidential documents.

Regulatory Compliance Management
We help you assess your organization’s and your third party’s level of compliance, and continuously monitor the applicable technical controls with industry security standards, such as PCI DSS, HIPAA, SOC 2, ISO 27001, NIST CSF / SP 800-53 / SP 800171, 23 NYC 500 and other customer-specific requirements. We also offer recommendations on how to remediate any gaps in compliance.
Learn more about compliance management powered by FortifyQuestionnaire.
