- Platform
Platforms
- Solutions
- Industries
Industries
- Why FortifyData
Why FortifyData
"This is an excellent starting point for any organization that wants to get serious about their cyber risk management. The system has the capability to grow as you become more sophisticated in your use"
IT Director
Services Industry - Company
Company
- Partners
Partners
- Resources
Resources
Security Ratings You Can Trust
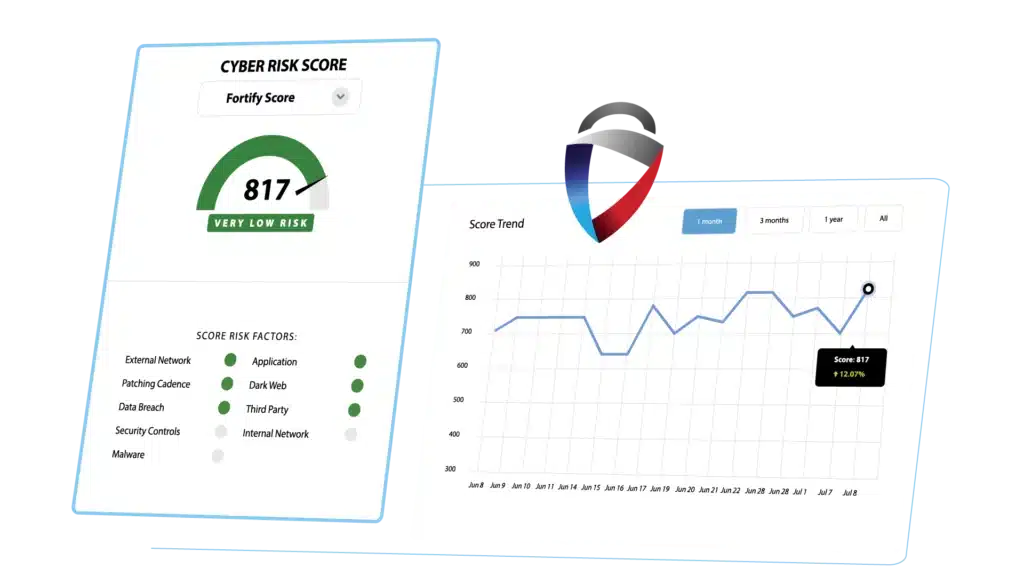
Ready for a frustration-free security ratings experience? FortifyData produces a more accurate security rating – eliminating misattributions, false positives, and lack of timely updates that you’ve experienced with other security ratings providers. We do this with automated and continuous discovery of your external enterprise and third-party risk and vulnerabilities.
We offer a complimentary cyber risk assessment on your organization to show you the power of our data. Or, you can jump straight to a demo.
“One of the problems I have with [different security ratings vendor] is that they find a domain with a low score and that domain is owned by someone else across the globe.”
“I have not seen a product that gives this level of automated threat assessment with the ability to conduct a proper quantitative and qualitative risk assessment.”
“I got a report from [different security ratings vendor], and I instantly knew it was incorrect because of misattributions and false positives.”
“Excellent, valuable platform! We bought FortifyData for accurate network scanning and reporting…I am beyond pleased with how well they work.”
Previous
Next
How Can I Improve My Security Rating?
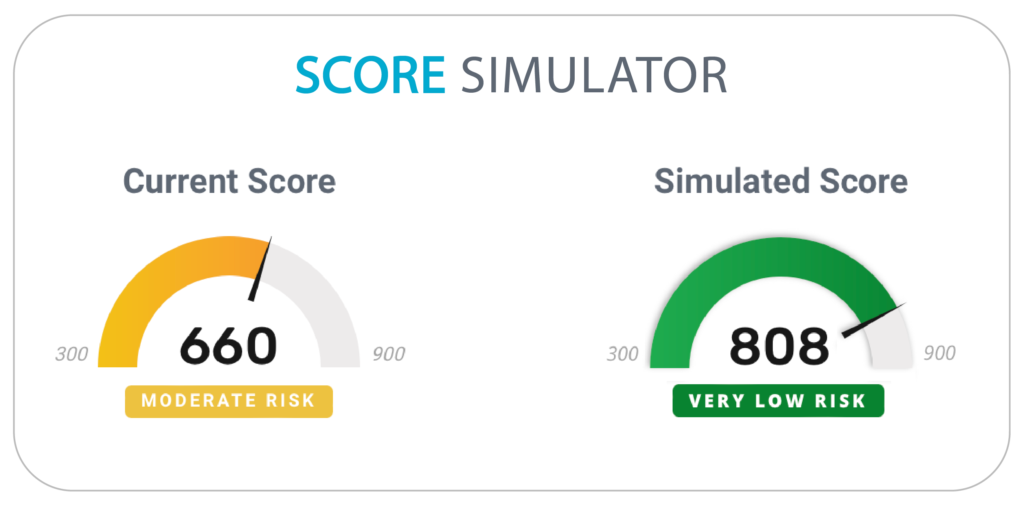
Use our interactive Score Simulator tool to test how mitigating or remediating certain risks will impact your security rating.
Within the tool, you can select specific risks and vulnerabilities that are present within your organization, and see how your score changes when the simulator identifies those risks have been fixed. Once you decide which risks you’d like to remediate based on the simulated score, you can create tasks to fix them or export the list of risks as a remediation plan.
How Does a FortifyData Security Rating Work?

Accurate Auto-Asset Discovery
Reduce asset misattributions with FortifyData’s auto asset discovery capability. While other solutions can take up to 4 months to update new asset inventory, we continuously search and identify new assets on a weekly basis.

Data Accuracy
FortifyData collects data through both active and passive assessment methodologies, not relying on historical, OSINT data. We continuously re-assess to make sure all attack surface data is timely and accurate.

Cyber Threat Intelligence
Our proprietary threat intelligence capability alerts clients when their business email credentials or data have been compromised from a third-party breach and available on the dark web. Through continuous dark/deep web scanning of files and databases across social media, un-indexed and transient deep websites, we will alert you of exposed company records, including leaked information, compromised credentials and confidential documents.

External Attack Surface Assessment
We conduct comprehensive, non-intrusive vulnerability assessments on your third-parties' attack surface on a weekly basis. These assessments produce accurate results using the most up-to-date vulnerability detection capabilities, allowing your organization to identify which vendors are susceptible to newer vulnerabilities, like log4j.

Standard and Custom Questionnaires
Achieve continuous compliance monitoring of your vendors with an automated process. Instantly send out standard or custom questionnaires, and get the full picture of risk using our auto-validation capabilities. Combining the assessment findings to auto-validate questionnaires saves time in reviewing third-party responses. This provides you with the answers you need more quickly (in the time to run an assessment) than a manual process. Easily assign tasks, collaborate and track questionnaire changes with our task management capabilities.

Configurable Scoring Model and In-Scope Assessments
FortifyData is the only platform that provides a configurable risk model, allowing you to create customized models based on factors related to your vendors' threat landscape. Clients can assign and modify factors attached to each cybersecurity risk category when calculating custom scores, getting a more accurate representation of the direct risk linked to your organization. You can also perform third-party in-scope assessments that focus only on assets and services relevant to providing services to your organization.
Configurable Scoring Model
FortifyData’s patented configurable scoring model presents a direct indication of breach susceptibility that considers the likelihood of threat scenarios, asset classifications and risk impact tot the organization. Clients can assign and modify weights attached to each cybersecurity risk category when calculating custom scores. This enables users to increase/decrease the relative impact of individual cybersecurity risks compared to the impact of these risks producing a more accurate view of the organization’s risk profile than using open source intelligence data.
300
900
An Alternative Security Ratings Provider for TPRM
Traditional ratings providers generally rely on a collection of externally available data or OSINT information that is collected from the internet. This may be network sensors, honeypots, ISP information. This is only a portion of your organization’s profile, but enough for them to generate a score. We think this leads to many inaccuracies and false positives nor does it allow for any customization based on criticality of the vendor or the specific services they provide.
FortifyData enables you to evaluate prospective vendors to understand data sharing risks, business continuity concerns and their overall cyber hygiene. You can even create additional custom risk scoring models that adjusts the weighting of specific risk scoring criteria related to a group of, or specific third parties. In addition to the rating, you can continuously monitor their evolving attack surface, embed those findings into standard compliance questionnaires, or custom questionnaires, to perform auto-validation that saves time in reviewing responses.
Why are Security Ratings Important?
The significance of security ratings lies in their ability to provide a concise and standardized measure of an organization’s susceptibility to cyber threats. These ratings are essential for several reasons:
Informed Decision-Making: Security ratings offer organizations insights into their digital risk landscape, aiding in making informed decisions about resource allocation and security investment. By identifying areas of weakness and potential vulnerabilities, organizations can prioritize their cybersecurity efforts effectively.
Third-Party Risk Management: Organizations often rely on third-party vendors for various services. Security ratings help in assessing the security posture of these vendors, allowing organizations to manage third-party risks effectively. This is crucial to prevent cyber threats from infiltrating the organization through less secure third-party connections.
Quantified View of Breach Susceptibility: Security ratings assist an organization (or an organization’s review of vendors) by providing a quantifiable rating – letter or score – that conveys a distilled metric of the organization’s cybersecurity posture based on external data of the organization. Monitor the security rating over time will show if an organization is improving, staying the same or declining. Many organizations have thresholds that a security rating should maintain and monitor as to how ‘risky’ they are and thus more susceptible to breach.
Methodologies of First-Generation vs. Next-Generation Cybersecurity Ratings
Data Collection: The foundation of any cybersecurity rating lies in the data it is based upon. Here it is important to distinguish first-generation security ratings providers from next-generation security ratings providers.
First generation ratings providers – likely large market leading providers – aggregate vast amounts of data from multiple sources, including publicly available open source (OSINT) information, threat intelligence feeds, ISP information, sinkhole, ARIN listings and more. This is only a portion of your organization’s profile, not very much of it is directly of your environment, but enough for them to generate a score.
Next-generation security ratings providers tend to focus more on direct, non-intrusive assessments of an organization’s infrastructure and applications, and will confirm asset inventory and supplement the information with passive assessment data, dark web findings. Additionally, the data may be further contextualized and enriched with other factors such as software vulnerabilities, network architecture, historical breach data, and patch management practices.
Weighting and Scoring: Once the data is collected, it needs to be processed and translated into a meaningful score. Different aspects of an organization’s cybersecurity posture are assigned weights based on their relative importance. For instance, a history of successful cyberattacks might carry more weight than the number of open ports on a server, application security risks, dark web findings, etc. These weighted factors are then used to calculate an overall cybersecurity risk score. Some of the security ratings providers do not provide a publicly available methodology, nor the ability to create additional security rating risk models where you can adjust the weighting of the factors important to your organization. For transparency, you can find our security ratings methodology here.
Industry Benchmark Analysis: Cybersecurity ratings are often more valuable when they provide a comparative analysis. This means that an organization’s rating can be benchmarked against industry peers or other entities with similar digital footprints. This industry, or peer, comparison allows organizations to understand how they fare in comparison to others and identify areas that need improvement.
Impact of Security Ratings
The applicability to provide a risk representation of your organization or a vendor and each unique risk profile is one thing. Similarly, security ratings can be used to inform additional use cases.
Cyber Insurance Premiums: In the realm of cyber insurance, some insurers are starting to incorporate cybersecurity ratings into their underwriting processes. Organizations with higher ratings might qualify for lower insurance premiums due to their demonstrated commitment to security. Here you can see where inaccurate ratings can translate to higher insurance premiums and more onerous process to refute an innacurate rating that an insurance provider may have of your company.
Mergers and Acquisition Interest: Security ratings are becoming an area of interest for investors. They use these ratings to assess the cybersecurity posture of companies they’re considering investing in. A higher rating can indicate a company’s proactive approach to mitigating cyber risks. More and more investors or companies pursuing Mergers and Acquisitions will include a security rating as part of their analysis as a way to judge any cyber liabilities they may be inquiring. Of course, further due diligence beyond just the rating will be examined prior to the closure of any deal. You may reacll Verizon was able to negotiate a lower acquisition price of Yahoo due to data breaches and undisclosed cybersecurity issues.
Security Program Monitoring: Security ratings, when agreed to be accurate representation of the organization’s risk, can be used as a monitoring tool for the cybersecurity program. As new vulnerabilities are discovered, assets detected teams can monitor their score knowing it will reflect any changes to the risks and vulnerabilities in their systems and assets and reflecting the organization’s continuous improvement program.
Challenges and Implications of Security Ratings
Accuracy and Data Quality: One of the key challenges with first-generation security ratings providers is ensuring the accuracy and quality of the data used for assessments. Inaccurate or outdated information can lead to skewed ratings that don’t reflect the true risk representation of an organization. Similarly, since the assessment to derive the score is not direct, mitigations and remediations may not reflect via an updated security rating score for months or quarters. Data quality assurance mechanisms are crucial to maintain the integrity of these ratings.
Lack of Standardization: The methodologies and criteria used for cybersecurity ratings can vary across different rating providers. This lack of standardization can lead to confusion for organizations trying to interpret their ratings or compare them across different platforms. This is also stymied by the lack of transparent methodologies (you can find our security ratings methodology here).
Without Accuracy, Expect a False Sense of Security: While first-generation security ratings were intended to provide valuable insights, they should not be considered the sole determinant of an organization’s security posture. Due to the inaccuracies that organizations are experiencing relying solely on ratings can lead to a false sense of security. Next-generation security ratings have arrived to provide a more accurate representation of risk through the use of direct assessments with confirmed assets. Those can then be supplemented with their own asset classifications, updated with latest vulnerabilities identified to their assets and enriched with cyber threat intelligence to get an accurate and up to date security rating.
Security ratings are evolving with the help of next-generation providers to be a more valuable tool in today’s cyber-threat landscape, offering organizations a quantifiable way to assess their digital vulnerability. By understanding and addressing the intricacies associated with these ratings, organizations can better fortify their digital defenses, make informed decisions, and build resilient security postures to navigate the complexities of the modern digital world.
What are the Best Security Ratings Providers?
The best security ratings providers are the ones that will accurately represent the cyber risk of your organization and be able to reflect mitigations and remediations that impact your score on a weekly basis. Would you agree?
The accuracy of the security rating is the most important aspect, you don’t want to add the frustration of defending or rebutting an inaccurate security rating to your security team’s plate. You want your security rating provider to be a trusted resource that provides accurate and timely risk intelligence for your company.
With FortifyData, you will have peace of mind knowing your security rating is calculated based on a transparent methodology, based on assets confirmed as your organizations and reflects remediations in a timely manner. There is no margin for error when it comes to cybersecurity and employing a security rating can help provide at-a-glance gauge on your program.
Resources
Explore more Resources >
Play Video




