Organizations now take an average of 204 days to identify and 73 days to contain a breach according to IBM’s Cost of a Data Breach report. That’s more than six months of potential exposure. For security teams, that’s simply unacceptable.
But there’s a way to eliminate it, and that’s by implementing a Continuous Threat Exposure Management (CTEM) platform to enable your threat exposure management strategy. The analyst firm Gartner even predicts organizations that adopt a CTEM strategy that “By 2026, organizations that prioritize their security investments based on a continuous exposure management program will be 3x less likely to suffer a breach.”
CTEM gives you a systematic, ongoing way to find and fix vulnerabilities, instead of reacting to every alert, before attackers exploit them. It’s not a single tool or a quick project, but a strategy built on a living process that blends visibility, validation and team mobilization.
So, if you want to be proactive, here’s how you can implement a CTEM security program.
Step 1: Establish Governance, Roles and Operating Cadence
Step 2: Assess Your Current Security Posture
Step 3: Define Scope, Objectives and Business Alignment
Step 4: Build an Integrated Technology Stack
Step 5: Establish Continuous Discovery and Monitoring
Step 6: Simulate and Validate Threat Scenarios
Step 7: Prioritize Exposures and Mobilize Remediation Based on Risk
Step 8: Measure, Report, and Communicate Outcomes
Step 9: Continuous Improvement and Expansion
How to Implement a CTEM Security Program
Every organization thinks they know their risks until a breach exposes the gaps in an asset or service it has overlooked. That’s why your CTEM journey must begin with a clear view of your current security reality and a defined plan for what comes next.
Step 1: Establish Governance, Roles and Operating Cadence
Before diving into tooling or inventories, organizations need clarity on:
- Who owns CTEM (Security? Risk? Cross-functional team?)
- Decision-making authority
- Risk tolerance and prioritization rules
- Cadence for exposure reviews (daily/weekly/monthly, depending on asset type)
We see that CTEM strategy adoption fails when it’s treated as “just another tool project.” It requires governance and repeatable cadence—essentially a program, not a product.
Step 2: Assess Your Current Security Posture
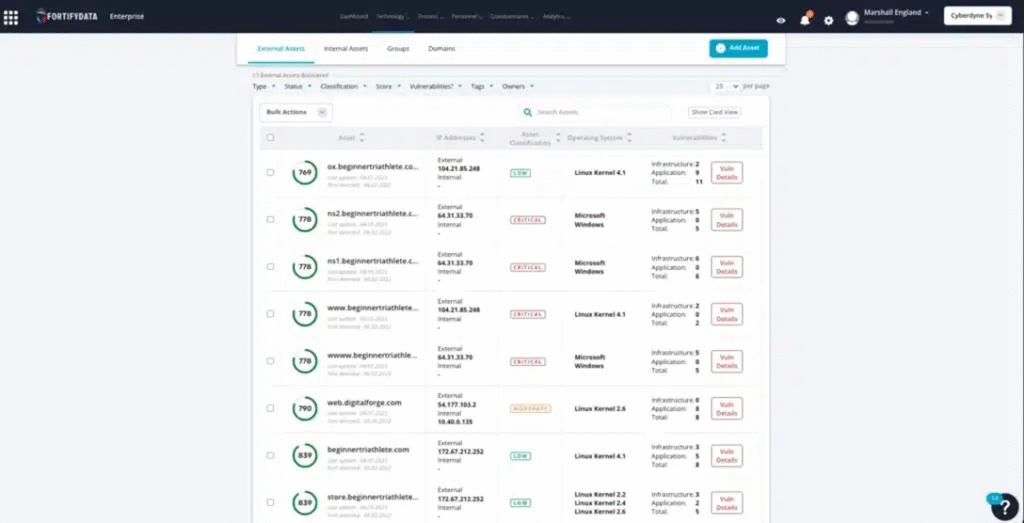
Every strong CTEM program begins with a deep understanding of the organization’s existing assets and services and the security environment in place to protect them. Before introducing new tools or workflows, you need to know what you already have and where the real gaps lie. CTEM builds on what you have; you need a baseline to know where to aim.
Start by performing a full risk assessment of your current infrastructure, such as networks, endpoints, cloud systems, and third-party connections.
Next, evaluate your current defenses. Determine how well your SIEM, SOAR, EDR/XDR and vulnerability management tools integrate and communicate. Many organizations find that these systems collect valuable information but fail to share it or the process to collate it and normalize it is too cumbersome and delayed to make timely risk-informed decisions.
Finally, involve your teams in this review. Analysts, engineers, developers, and risk managers often understand where inefficiencies exist better than any dashboard can show.
Step 3: Define Scope, Objectives and Business Alignment
With visibility in place, it’s time to shape the direction. A CTEM security strategy without a defined scope can easily drift into endless scanning without real results. Setting clear boundaries gives your efforts focus and purpose.
Begin by defining which areas truly matter; not every system needs the same level of scrutiny.
Ask:
- Which assets are business-critical, “crown jewels”?
- Where could a single failure disrupt operations or customer trust?
- Are there areas of segmentation to contain issues should they arise?
- Which third parties have access to sensitive data?
- Who needs to be contacted when certain services or assets are disrupted? Are they in-house or external?
Once those are clear, decide how deep you’ll go. Some organizations start with external assets only, while others include cloud workloads or internal applications right from the start.
Remember, this phase isn’t about ambition alone. CTEM is iterative. A narrow, business-aligned scope accelerates early wins.
It’s about creating a framework that your team can realistically sustain, measure, and scale as the organization grows.
Step 4: Build an Integrated Technology Stack
Once your goals are set, it’s time to connect the dots. CTEM doesn’t work in isolation. It thrives when every part of your security ecosystem speaks the same language.
For that, you should start by linking your existing tools. For instance, SIEM for event logging, SOAR for automated workflow, EDR for endpoint detection, and attack surface or vulnerability scanners for exposure tracking.
CTEM requires these traditionally isolated systems to be connected so they can feed each other meaningfully. For example, attack surface discoveries should automatically enrich internal vulnerability data; threat intelligence should provide real-world exploit context; business asset criticality must feed into prioritization; and remediation workflows should automatically trigger based on validated exposures. The goal of this step is to create an ecosystem where the security stack is interoperable, context-aware, and streamlined, not redundant. In many cases, this means reducing the number of tools—not increasing them—and choosing platforms that unify ASM, risk-based vulnerability management, continuous monitoring, and workflow automation so the CTEM cycle can run continuously and efficiently.
When these systems share context in real time to a centralized management area, you eliminate blind spots that attackers often exploit. Your CTEM program shows its real strength when your tech stack functions as a cohesive unit.
Step 5: Establish Continuous Discovery and Monitoring
Now that your tools are connected, the next step is to keep the picture alive. Cyber environments evolve every minute, and static scans are no longer enough. Continuous discovery ensures you always know what’s connected, what’s changed, and what’s at risk.
CTEM operates on the assumption that exposure changes constantly. Continuous discovery is its heartbeat.
Every asset should be visible and accounted for. Many breaches happen because a forgotten system wasn’t patched or monitored.
Companies can easily avoid that with continuous discovery. Here’s what you should focus on:
- Asset Discovery: Track every endpoint, user, and application as they appear.
- Real-time Visibility: Use sensors or agents to detect changes in configuration or access.
- Anomaly Alerts: Identify unusual behaviors early, before they turn into incidents.
When your visibility stays fresh, your defenses can adapt just as quickly as attackers evolve. That’s what gives CTEM its “continuous” edge; it’s never just a one-time scan but an always-on process of awareness and action.
Step 6: Simulate and Validate Threat Scenarios
Once visibility is strong, it’s time to test how well your defenses actually hold up. Many organizations assume their systems are secure just because no incidents have occurred. That’s a dangerous illusion.
Validation exposes how your security controls behave under real-world conditions. Here’s when you run controlled simulations such as red teaming, breach and attack path simulations, and adversary emulation.
This validation step, a pillar in the Gartner definition, is what separates a CTEM strategy from traditional vulnerability management.
Each test gives you a glimpse into how attackers might move inside your environment if they ever got in. For instance, a simple phishing simulation might show that 12% of your users still click suspicious links or an innocuous vulnerability on their own isn’t very exploitable, but when daisy-chained with additional vulnerabilities can be devastating to your business. That insight tells you where training needs to improve and how to think about collections of asset vulnerabilities.
Step 7: Prioritize Exposures and Mobilize Remediation Based on Risk
Now comes the decision-making stage. Here, you need to turn all that data into smart action. Not every threat deserves equal attention, and trying to fix everything at once usually leads to burnout and wasted effort. This step helps you focus on what truly matters.
Based on the previous exercise of identifying the priority of business-critical assets and services, this helps rank vulnerabilities according to impact and likelihood. Ask: If this asset were compromised, how much damage could it cause? Does it directly affect critical operations, financial data, or customer trust?
Prioritization gives clarity when everything feels urgent.
Then move into remediation, step by step. Address the highest-risk areas first, especially those exposed to the internet, compromised third party vendors, or tied to sensitive systems. For lower-risk issues, create timelines and automate fixes where possible.
Step 8: Measure, Report, and Communicate Outcomes
Once your CTEM program is running, measurement becomes your guiding compass. Without tracking results, it’s impossible to know what’s improving and what still needs work.
Here, you require metrics that reflect your program’s progress. For instance, track Mean Time to Remediate (MTTR), the number of exposures closed per cycle, and how many simulated attacks were detected versus missed.
It’s also important to turn these technical insights into language that business leaders can understand.
Instead of saying “we fixed 250 vulnerabilities,” frame it as “we reduced potential data exposure by 40% this quarter.” And here is why those exposures were more important than these other exposures.
Step 9: Continuous Improvement and Expansion
After initial scope maturity, your feedback loops should begin incorporating expansion of other threat exposure sources like cloud, identity, OT, third parties.
- Integrate new data sources
- Improve automation/AI decisioning
- Feed lessons learned back into governance and risk appetite
Gartner stresses CTEM as a programmatic cycle that improves each iteration.
Ready to Make CTEM Happen for Real?
You’ve seen how continuous threat exposure management works in theory, but what if you could bring it to life without juggling a dozen tools?
That’s exactly what we built at FortifyData.
Instead of switching between platforms and spreadsheets, you can see your entire attack surface in one view. You can spot vulnerabilities before attackers do, validate fixes automatically, and stay compliant without the constant manual effort.