
Whitepaper: AI-Powered Next Generation Third-Party Risk Management In an increasingly interconnected digital ecosystem, third-party vendors are both essential enablers…
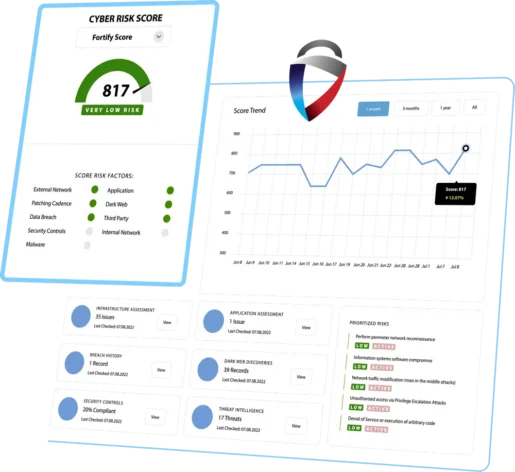
Ensure nothing is missed as we continuously map and monitor your entire attack surface
Automated attack surface assessments continuously identify new exposures aligned with your business criticality so your organization can proactively protect against unauthorized intrusions. Focus on what matters most with context based prioritization to expedite remediation.

Tired of reading SOC 2 reports? Save time with AI Audit Dashboard
Upload vendor provided reports and get an AI-powered audit analysis of their report against the principles or controls.
Combining AI-powered report analysis, with agentic vendor management workflows for questionnaires and external assessments of vendors, your TPRM program will take less time and identify the risks you use to spend hours trying to find.

Save time and resources to achieve and maintain compliance.
Automate the tedious tasks of compliance monitoring and reporting, freeing up your team to focus on proactive security while reducing the risk of non-compliance. With risk findings natively assessed and monitored, we seamlessly tie them to applicable framework controls and continuously report on them.

Your operational context drives the likelihood and impact
Our AI-powered risk prioritization understands taht some systems and assets take a priority. Now your team gets a real-time ‘fix list’ with intelligently recommended remediation steps to reduce the most critical risks facing your organization.

The days of $3M GRCs and years to implement are over
Streamline your cybersecurity compliance journey with the advantages our AI-powered platform. Integrate the continuous attack surface, remediation, and third-party risk findings into your compliance and audit program. Save time and resources with a consolidated platform with unified data that seamlessly feeds to your controls.





Gain real-time visibility and stay ahead of threats with intelligent risk insights and remediation workflows.
Cyber GRC – Unify governance, risk, and compliance specifically for cybersecurity use cases
Enterprise Risk Management – Centralize risk oversight across departments and functions
Internal Risk Assessments – Automate assessments and evidence collection for stronger internal controls
Identify and mitigate risks across your infrastructure and vendor ecosystem with continuous monitoring.
Attack Surface Management – Eliminate blind spots with complete asset visibility
Vulnerability Management – Detect, prioritize, and remediate vulnerabilities faster
Security Rating – Monitor your own security posture and benchmark against peers
Strengthen your supply chain with continuous vendor monitoring, automated risk scoring, and real-time attack surface data that goes beyond static questionnaires.
We continue to win business and provide superior value to our clients who preferred the FortifyData approach compared to Security Ratings or Attack Surface Management (ASM) vendors.


FortifyData is a specialized grc software solution tailored to cybersecurity and compliance teams. It helps organizations eliminate tool sprawl, improve visibility, and reduce cyber risk—without the complexity of traditional GRC platforms.


FortifyData delivers specialized GRC software solutions that adapt to the unique risk and compliance needs of every sector. Our unified GRC platform helps organizations across industries strengthen cybersecurity, streamline compliance, and reduce risk.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |