How Pima Community College Strengthened Its Attack Surface Management with FortifyData

How Pima Community College Strengthened Its Attack Surface Management with FortifyData https://youtu.be/yAJs9kCxmCw Challenge Pima Community College struggled with comprehensively tracking its entire attack surface comprehensively, leading to vulnerabilities being overlooked and not addressed promptly. Key Results FortifyData clearly demonstrated not just the presence of vulnerabilities but also their potential impact and likelihood, making it evident […]
EDUCAUSE Demo Day: Cybersecurity Tools – February 2024

EDUCAUSE Demo Day: Cybersecurity Tools The FortifyData platform helps higher education institutions automate cyber threat assessments, contextualize risks for prioritization, and evaluate vendor cyber risks to make cybersecurity risk and compliance management more efficient and proactive, enhancing protection against evolving cyber threats. Enjoy this on-demand demonstration that was conducted for a Demo Day with EDUCAUSE. […]
FortifyData and Lansweeper Announce New Integration to Enhance Cyber Risk Management

FortifyData and Lansweeper Announce New Integration to Enhance Cyber Risk Management November 28, 2023 KENNESAW, GA, November 28, 2023 – FortifyData, a leading provider of cyber risk management solutions, is excited to announce its newest integration with Lansweeper, an expert in IT Asset Discovery. This partnership is set to expand the availability of cyber risk […]
How This Community College Successfully Achieved Safeguards Rule Compliance and Cybersecurity Automation

How This Community College Successfully Achieved Safeguards Rule Compliance and Cybersecurity Automation Challenge The College of the Canyons recognized the growing need for an effective cyber risk management program to safeguard its digital environment against the backdrop of an increasingly perilous cyber landscape and make progress towards meeting various regulatory compliance requirements, like the Safeguards […]
Fortifydata anuncia a disponibilização do Quadro Nacional de Referência para a Cibersegurança para infraestrutura crítica
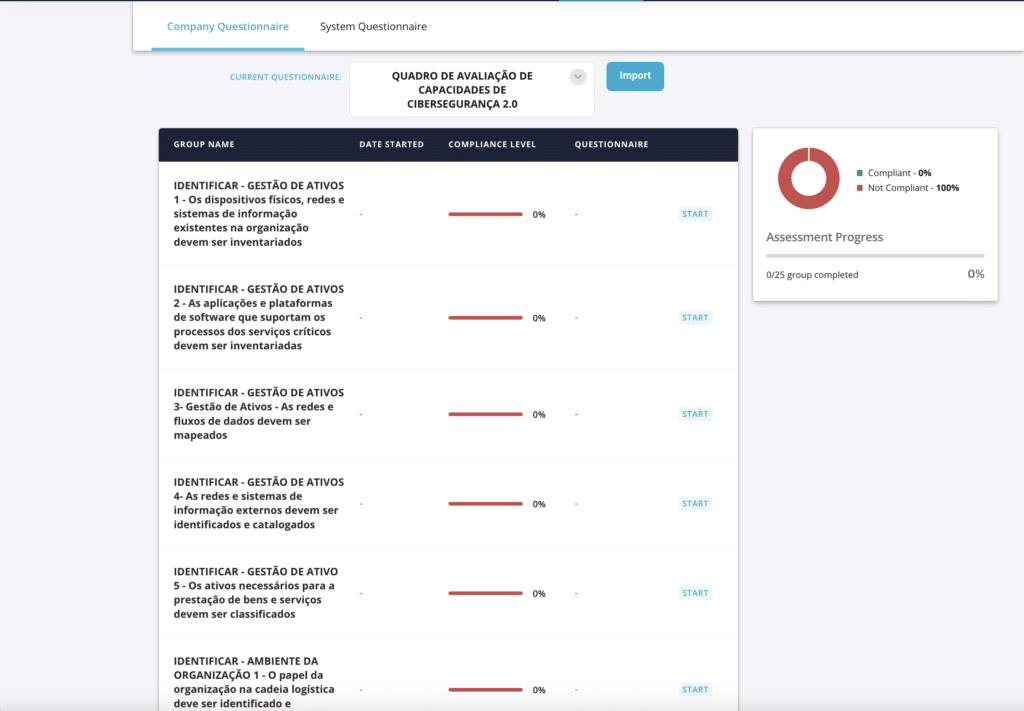
Fortifydata anuncia a disponibilização do Quadro Nacional de Referência para a Cibersegurança para infraestrutura crítica November 21, 2023 KENNESAW, GA, November 21, 2023 – A Fortifydata tem neste momento integrado na sua plataforma o QNRCS, para permitir que as empresas consigam avaliar o nível de maturidade, gerir, monitorizar, a cumprirem os respetivos requisitos do Quadro […]
FortifyData Announces the Availability of the Quadro Nacional de Referência para a Cibersegurança Assessment for Portuguese Critical Infrastructure

FortifyData Announces the Availability of the Quadro Nacional de Referência para a Cibersegurança Assessment for Portuguese Critical Infrastructure November 21, 2023 KENNESAW, GA, November 21, 2023 – FortifyData is pleased to announce that we can assist businesses in meeting the stringent requirements of the Quadro Nacional de Referência para a Cibersegurança (QNRCS). Understanding QNRCS The […]
Higher Education Demo Day: Automating Cyber Risk Management Enriched with Cyber Threat Intelligence

Higher Education Demo Day: Automating Cyber Risk Management Enriched with Cyber Threat Intelligence Earlier this year the research firm Gartner identified Top Technology Trends impacting Higher Education and incorporating cyber threat intelligence into their overall cybersecurity risk management was one of those trends. In this demo day webinar see how FortifyData can simplify the collection […]
Webinar: Automating Cyber Risk Management

Webinar: Automating Cyber Risk Management Watch the On-Demand Webinar With increasing threats, challenging economic environments, budget limitations, and cyber talent shortages, how can security leaders efficiently manage cyber risk at scale? This session discusses opportunities for identifying, automating, and prioritizing cyber risk throughout an organization’s attack surface, including third parties. Watch to learn: What opportunities […]
Federal Government Drivers for Supply Chain Security

Federal Government Drivers for Supply Chain Security Policy, Regulations, and Requirements Focused on Supply Chain and Third-Party Risk WHITEPAPER > Understand the different regulations with third-party specific control requirements > Discover how to approach third-party cyber risk management to meet Federal requirements > Learn how to implement automation to rapidly deliver value in your TPCRM […]
Forrester VRM Landscape Report 2023

Vulnerability Risk Management Landscape, Q2 2023 FORRESTER REPORT > Updated trends for VRM use cases to include asset classification, enrichment with threat intelligence for prioritization > Learn about the notable vendors in the space along with their focus areas and use cases for shortlisting > Discover the VRM functionalities that are most essential for both […]
