How to Implement a CTEM Security Program in Your Organization

Want to build a CTEM security program that actually works? Learn the steps to build continuous protection and stay ahead of cyber threats.
Automating Trust — How FortifyData Reinvents Third-Party Cyber Risk Management
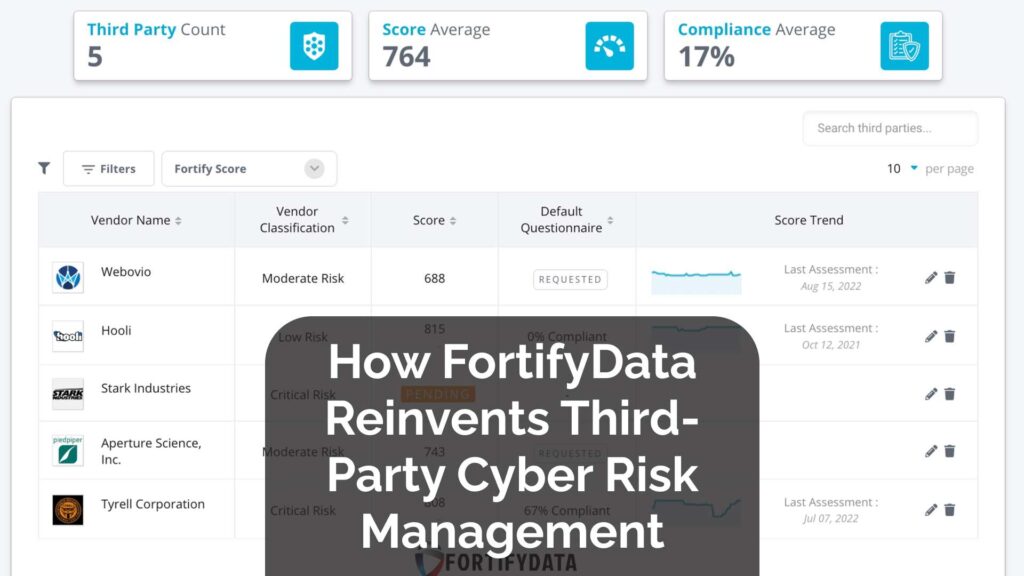
Explore how FortifyData reinvents third-party vendor risk management with AI and automation.
The CTEM Framework: Core Pillars Every Organization Should Know
Wondering what makes CTEM framework powerful? Discover its core pillars and learn how organizations can strengthen cybersecurity with this modern approach.
Introducing FortifyData’s Incident Management Module: From Chaos to Clarity
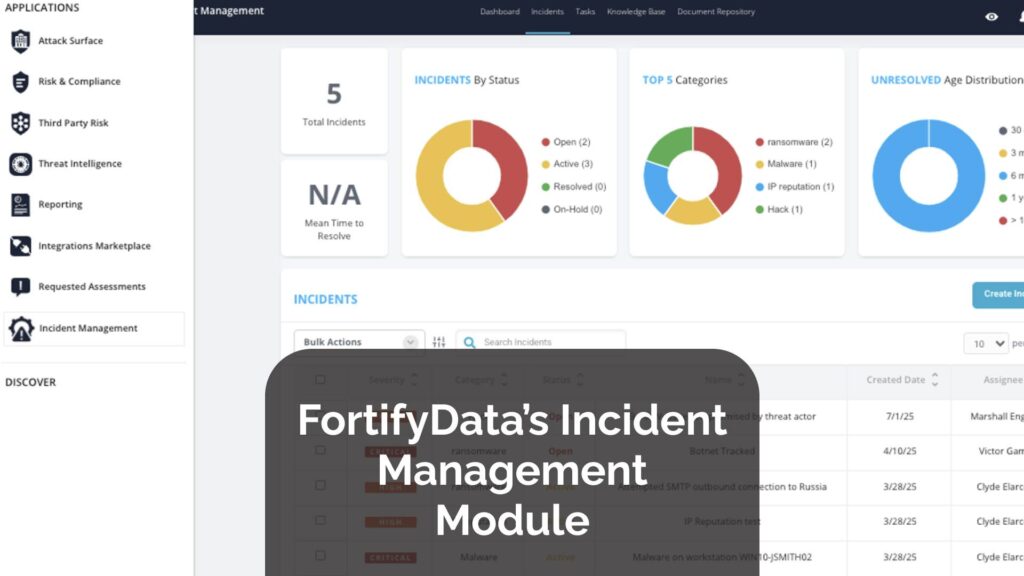
Streamline incident response with FortifyData’s incident management module—log, track, and resolve incidents faster while staying audit-ready and compliant.
How Universities Can Prevent Financial Data Breaches

Discover practical strategies universities can use to protect financial data, prevent cyberattacks, and strengthen campus-wide data security from the ground up.
How Colleges and Universities Can Improve Cybersecurity Training

Learn how higher education institutions can enhance cybersecurity training for students and staff with proven strategies and best practices.
Navigating NIS 2 Compliance: Challenges for Companies and How MSSPs Powered with FortifyData Can Help

The European NIS 2 compliance and regulation scope includes small & mid-sized companies in more sectors.
Higher Education One Year After MOVEit: Lessons Learned and Evolving Vendor Risk Management

What has changed in the higher education industry and vendor management one year after the MOVEit file transfer software vulnerability.
What are the 5 Main Threats to Cybersecurity?

5 main threats to cybersecurity: Phishing or social engineering, malware, ransomware, deep fakes, supply chain attacks.
Managing Enterprise-wide and Departmental Cyber Risk in One Platform

This blog explores the immense value of having a cyber risk management platform.
