Gartner introduced the concept of Continuous Threat Exposure Management (CTEM) in 2022 (link to article) and since then the global average cost of a data breach hit $4.88 million.
Gartner’s intent was to establish a framework that shifts organizations from reactive, point-in-time vulnerability management to an ongoing, risk-driven exposure management model. For organizations that adopted a CTEM strategy they predicted that “By 2026, organizations that prioritize their security investments based on a continuous exposure management program will be 3× less likely to suffer a breach.”
That should be a wake-up call for every organization that’s still relying on outdated defenses.
So, what’s the solution to not being exposed to such cyberthreats? Continuous Threat Exposure Management (CTEM).
It is a structured approach to consistently identify, assess, and address security gaps before attackers can exploit them. But to use it effectively, you need to understand the core pillars that make CTEM work.
Here’s what you need to know about it.
What Is the CTEM Framework?
The CTEM framework is a method for organizations to manage cyber security risks before they escalate into actual attacks. As you will learn, the CTEM strategy is cyclical and continuous with the outputs and lessons from one iteration fed back into refining scope, discovery, and prioritization in subsequent rounds. It becomes a virtuous cycle for your cybersecurity program.
Instead of reacting only after something goes wrong, CTEM helps you continuously identify weaknesses, test which ones are dangerous, and address them promptly. This ongoing process keeps security teams proactive and reduces surprises.
The 5 Core Pillars of CTEM Framework
Let’s break down the five core pillars or five phase model of CTEM in the simplest terms, so you can see how they connect and why they matter.
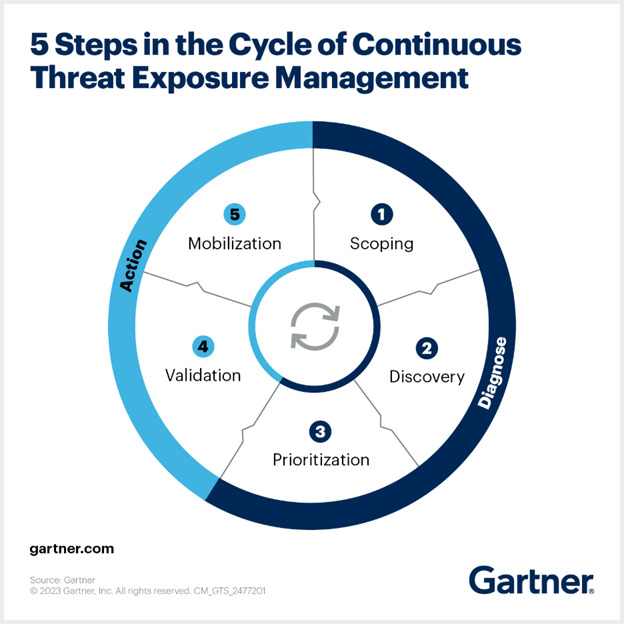
Pillar #1: Scoping
Every strong CTEM program starts with scoping. It’s about defining the boundaries of what needs protection. Without it, you risk spreading your resources too thin or missing critical blind spots.
In CTEM, scoping means defining the boundaries of the environment you want to assess. This could be:
- A specific business unit
- A cloud environment with sensitive data
- Critical applications that customers rely on
It’s not about trying to secure everything equally, but focusing on where the real damage could happen if attackers got in. For instance, a financial services company might prioritize systems handling payment transactions over less critical internal apps.
Why is this step so important?
Because 45% of cyber incidents involve cloud-based resources. So, if you don’t clearly scope these environments, you might leave critical attack surface blind spots.
Pillar #2: Discovery
Once you know what to focus on, the next step is discovery. Imagine shining a flashlight on every asset, vulnerability, and misconfiguration within that scope.
This step is about visibility. You cannot protect what you don’t know exists. Discovery uncovers:
- Servers, applications, and databases
- Weak configurations, like open ports or weak passwords
- Shadow IT, such as employees using unauthorized apps
- Forgotten systems that still connect to your network
Ponemon Research shows that 60% of breaches come from unpatched vulnerabilities. Many of these were not hidden secrets but were simply overlooked or never discovered in time.
A good discovery process runs continuously, not just once a year. Organizations are realizing the need to evolve their programs from pont in time to continuous threat exposure management.
How FortifyData helps with Discovery
Continuous Asset Discovery: Automatically identifies domains, IPs, subdomains, and exposed services across your entire digital footprint—including shadow IT.
Pillar #3: Prioritization
After discovery, you’ll likely have a long list of exposures. But here’s the problem: not every rusk is equally dangerous. When you try to fix them all at once, it becomes overwhelming and wastes effort.
That’s why the CTEM framework emphasizes prioritization. In simpler terms, this means ranking exposures based on two main things:
- Business Impact: Would exploiting this exposure harm customers, revenue, or compliance?
- Exploitability: Can attackers realistically take advantage of this vulnerability?
For example, a critical server with a zero-day vulnerability should jump to the top of the list, while a slightly misconfigured internal printer can probably wait.
In fact, studies show that fewer than 10% vulnerabilities are never actually exploited. This means if your organization has 10 vulnerabilities, 9 of them will definitely be exploited.
So why chase all of them equally?
How FortifyData helps with Priortization:
Risk-Based Prioritization: FortifyData combines threat intelligence, exploitability, asset value, and considers compensating controls to prioritize vulnerabilities that pose real risk.
Pillar #4: Validation
Validation is what makes CTEM different from traditional vulnerability management. It asks a simple but powerful question: “Is this risk actually exploitable?”
Instead of assuming every flagged vulnerability is dangerous, validation tests whether attackers could really use it.
This can involve the next step after vulnerability management:
- Automated validation tools
- Red-team simulations
- Penetration testing
- Exploit testing in controlled environments
So, what’s the main benefit of this pillar?
It identifies which vulnerabilities are critical, as studies show that only 32% of vulnerabilities found in any system are exploitable. That means most of what scanners flag won’t realistically be used by attackers.
Remember, without validation, teams waste time chasing ghosts. With validation, you focus only on exposures that truly matter.
Since CTEM is meant to be continuous and cyclical, returning to previous exposures to validate that they are indeed remediated improves your security posture through this validation phase.
How FortifyData helps with Validation:
Live Data, Not Snapshots: FortifyData conducts full vulnerability scanning, all 65,636 ports and services, are conducted weekly or more frequently to provide up-to-date visibility, new asset identification and changes into new exposures and confirmation that previous exposures have been mitigated. Each finding we identify includes actionable steps, helping teams close gaps quickly and efficiently.
Pillar #5: Mobilization
The final pillar is where the real magic happens. This is about turning insights into pure action against vulnerabilities.
Mobilization involves:
- Patching critical systems quickly
- Adjusting security configurations
- Updating policies and procedures
- Training employees if human error is part of the exposure
This pillar phase is about execution.
Implement corrective actions—such as patching, configuration updates, or control enhancements—through established workflows and automation where possible. The goal is to remediate validated exposures efficiently while feeding lessons learned back into the next CTEM cycle.
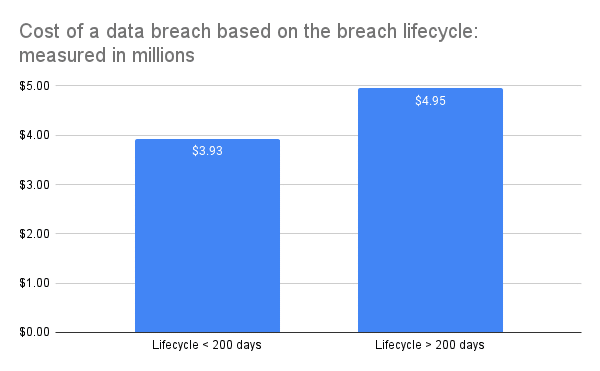
Finding and prioritizing risks is meaningless is nothing changes. And speed makes a big difference; as IBM found that breaches contained in under 200 days cost $1 million less than those that drag on.
For instance, a CTEM-driven team might detect and patch a critical vulnerability in hours. Without CTEM, that same issue might linger for weeks and give plenty of time for attackers to exploit it.
How FortifyData helps with Mobilization:
FortifyData enables organizations to close exposures faster through native workflow communication or integration with existing ticketing solutions to reduce friction across security and IT teams. This assists in continuously feeding insights back into the next exposure management cycle for measurable risk reduction.
Take Control of Cyber Risks Before They Control You
Gartner introduced CTEM as a framework for continuous threat exposure management — and many organizations now adopt it as a strategy for reducing cyber risk year-round.
Every organization today faces a common problem that cyber threats are evolving faster than ever. Due to this, manual processes and reactive strategies leave gaps that attackers exploit in the long run.
This is where you need to be smarter and FortifyData help you do just that. Our software solution for CTEM strategy implementation changes the game by helping you see your risks clearly, prioritize what truly matters, validate real threats, and take swift action.
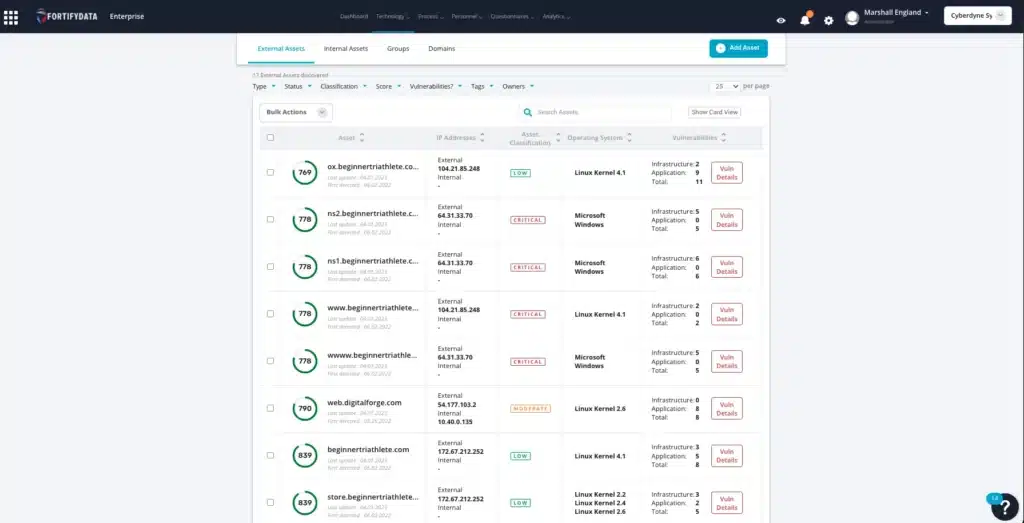
Request a demo today and see how our CTEM solution can help!
FAQs
1. Can CTEM replace my existing security tools?
No, CTEM isn’t about replacing your entire security stack. Instead, it works as an integrated approach that makes better use of what you already have, in some cases that could lead to replacing or removing tools. It consolidates data from scanners, cloud platforms, and monitoring tools, then organizes it into actionable priorities.
2. How does CTEM help with regulatory compliance?
Compliance frameworks like GDPR, HIPAA, and PCI DSS require organizations to continuously monitor and reduce risks. CTEM aligns perfectly with this by automating scoping, discovery, and remediation. Instead of scrambling to prepare for audits, you already have real-time data.
3. How often should exposures be validated under CTEM?
Validation should be an ongoing process. With CTEM, exposures are continuously tested against real-world exploitability. For example, if a vulnerability appears in your cloud platform today, CTEM ensures it’s validated immediately, so you don’t waste time fixing something that isn’t exploitable.