Ever wonder why your cybersecurity tools don’t stop every breach?
The problem may lie in not knowing the difference between attack surface vs attack vector. The issue might be a lack of clarity between your attack surface vs attack vectors. So, what are attack vectors?
You need to understand what each one means as it relates to the types of attack surfaces in cybersecurity to anticipate how attackers might target your systems. Let’s put it this way…your attack surface is likely an attack vector.
So, let’s explore how to reduce this risk and protect what matters most.
What is an Attack Surface?
Your attack surface represents all the possible points where an unauthorized user could enter or extract data from your systems. Think of it as the digital entryway to your house; it includes open ports, software interfaces, exposed APIs, and misconfigured cloud services.
Modern organizations face complex IT infrastructures. These include IoT devices, hybrid cloud environments, and third-party SaaS tools. Without a clear map of this surface, it becomes nearly impossible to rate security and defend it effectively.
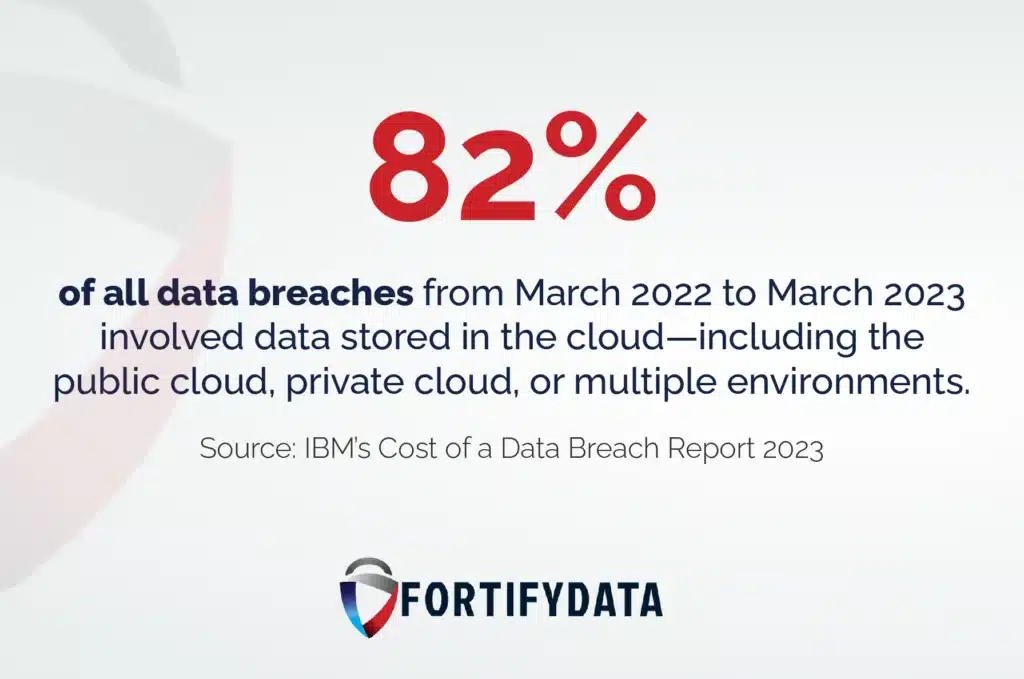
What is attack surface management? The attack surface definition in cybersecurity often refers to all exposed areas of a system that are accessible to threat actors. One of those is the data stored in your cloud environment, which, according to and IBM study, is involved in 82% of the data breaches.
What is an Attack Vector?
On the other hand, an attack vector is the method or pathway that an attacker uses to exploit weaknesses in an organization’s system. It’s how they penetrate your organization and then navigate within it once they gain access. Vectors include phishing emails, malware downloads, SQL injection, exploiting unpatched/un-mitigated vulnerabilities, and social engineering.
The attack vector’s meaning becomes even more important in cyber defense when organizations face frequent attempts like ransomware or credential stuffing. For example, attack vectors in cybersecurity often rely on exploiting human errors, such as clicking on malicious links or combining various vulnerabilities with an attack surface and internal systems so they gain access and move laterally within to gather intelligence, garner further access or deliver a malicious payload.
According to Verizon’s 2024 Data Breach Report, 74% of breaches involved the human element. That shows how much trouble human errors cause for businesses.

The attack vector definition is typically contextual, ranging from malicious links to unauthorized USB device usage. Knowing your attack vectors helps your team prioritize defenses.
Struggling to detect vectors before getting exploited?
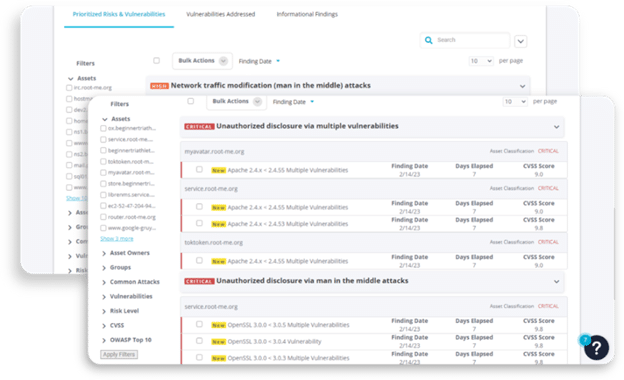
FortifyData’s Attack Surface Management (ASM) is here to offer real-time visibility into your exploitable assets and attack paths that you’re not aware of.
Attack Surface vs Attack Vector
The terms attack vector vs attack surface often get used interchangeably especially if you are beginning your career in information securty, but they serve different roles in a security strategy. The confusion leads to blind spots in cyber defenses. Some companies believe managing one automatically secures the other. That’s not the case.
Consider a web server with outdated software. The attack surface threat here is the unpatched server itself, which is part of your attack surface. Cyber security attack vectors are a remote code execution exploit targeting that outdated software.
Mapping the Difference
| Feature | Attack Surface | Attack Vector |
| Definition | All possible points of unauthorized access | The method used to gain unauthorized access |
| Nature | Static or dynamic as assets grow | Varies, relies on the attacker’s strategy based on reconnaissance of your organization |
| Examples | Open ports, misconfigured APIs | Phishing, vulnerability exploitation, and zero-day exploits |
| Scope | System-wide | Action-specific |
| Preventive Measures | Surface reduction, attack surface management | Vector-specific threat detection |
Security Blind Spots in Action
Many organizations fail to distinguish between the two and focus only on detection. For instance, securing endpoints while leaving API access open expands the threat vectors unintentionally. This is where threat modeling excersices for your organization can really help strengthen your attack surface defenses against higher-risk attack vectors that can have a detrimental effect on your organization.
You may think your firewall is enough, but if attackers exploit a cloud misconfiguration, you’ve missed the bigger threat surface. In fact, a staggering 82% of enterprises experienced security incidents due to cloud misconfigurations, highlighting how common these gaps are.

This shows how easily an exposed API or unsecured storage bucket becomes both a weak surface and a direct successful cyber attack vector.
Smart Defense Starts with Clarity
Reducing your security attack surface should start with asset discovery. The fewer public-facing elements, the smaller your exposure. Tools like external surface risk management platforms offer this capability.
Simultaneously, threat intelligence systems monitor active attack vectors. Machine learning models now detect anomalies in traffic or behavior that match vector patterns. Pairing these systems ensures a double layer of protection.
Attack vector definition in cybersecurity takes a contextual turn here. A vector for an e-commerce app might be payment skimming scripts. However, for an enterprise, it could be spear-phishing campaigns targeting C-suite executives.
Protect Your Entire Attack Surface Now
Cyber threats are not going to slow down anytime soon. And the debate of attack surface vs attack vector will continue. But remember, the cost of confusion between an attack surface and an attack vector could be your business itself.
That’s why you need a system that identifies your attack surface, maps it, and simultaneously detects which cyber security attack vectors have a higher risk for your operational resilience.
And that’s where FortifyData shines.
With our Attack Surface Management solution, you don’t have to choose between surface visibility and vector defense among the types of attack surfaces in cybersecurity; you get both. The platform closes the gaps before attackers can exploit them.
Schedule a free demo today!
FAQs
1. Does reducing the attack surface reduce attack vectors?
Yes, reducing your attack surface directly reduces potential attack vectors. The attack surface includes all entry points that hackers can use. When you close or secure those points, you take away the paths attackers might use. Fewer exposed points mean fewer ways to get in.
2. What tools help monitor both the attack surface and vectors?
Attack Surface Management (ASM) platforms like FortifyData help with both. They scan your entire digital footprint to find exposed assets and risks, then track active attack vectors like exploits, malware delivery paths, and vulnerabilities.






