AI Auditing, Workflow Automation, and Defensible Risk Decisions
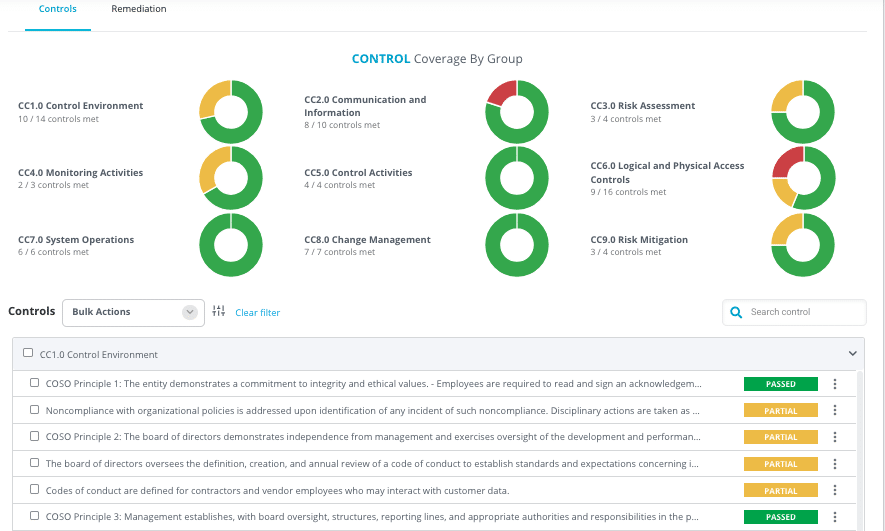
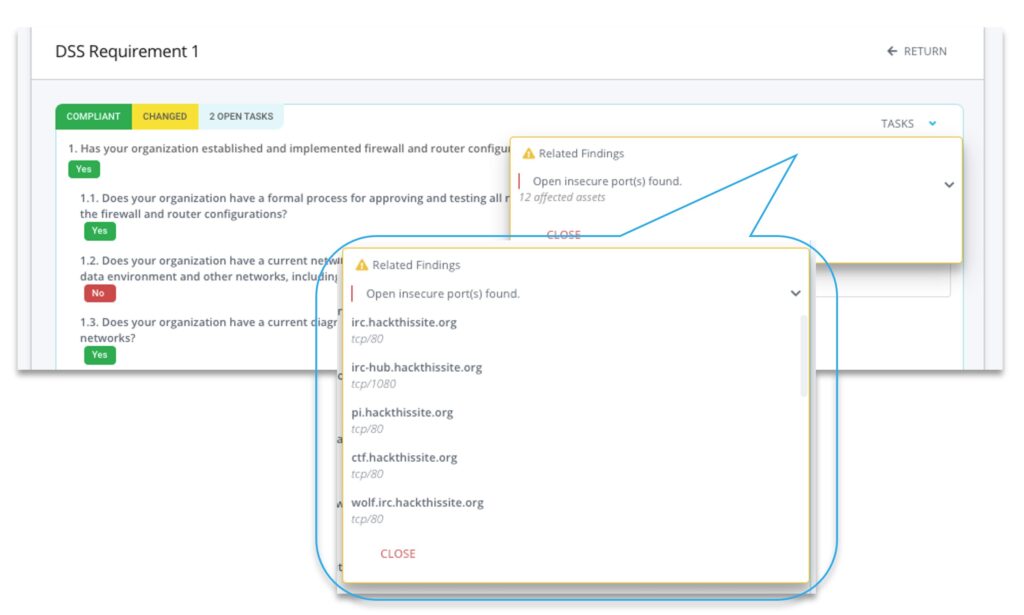
Most third-party risk programs do not struggle due to a lack of assessments — they struggle because security teams cannot efficiently analyze, validate, and operationalize the growing volume of third-party risk evidence.
Read on about automated and continuous external assessments of vendors, AI Auditor of SOC 2 and other vendor reports, workflow automation and intelligent questionnaire management and auto-completion.