Do you know 27% of organizations experienced a public cloud security incident last year?
It’s because the cloud attack surface is rapidly growing in companies, which include all internet-exposed assets tied to your cloud environment.
But even though today’s cloud offers speed and scale, they are not without risks. That’s why in this article exploring this types of attack surfaces in cybersecurity, we’ll explore what’s included in your cloud attack surface, what the risks are, and how you can save yourself from them.
What Is the Cloud Attack Surface?
Let’s examine the cloud attack surface as part of our What is Attack Surface Management: Complete Guide and Best Practices guide.
The cloud attack surface includes all the internet-facing parts of your cloud setup. These are the systems attackers can find and try to exploit. It covers APIs, storage buckets, virtual machines, containers/k8s, identity tools, databases, and more.
In the cloud, everything is fast and decentralized. Services launch quickly, teams move fast, and many parts run across different regions and availability zones. This can make it difficult to track and secure everything simultaneously.
Gartner predicts that by 2025, 99% of cloud security issues will stem from inadequate setup and lack of customer knowledge.

Five Top Cloud Attack Surface Risks
These are the most common cloud attack surface management vulnerabilities that attackers exploit when cloud environments aren’t properly secured.
1. Misconfigured Cloud Storage
Cloud storage services, such as AWS S3, Google Cloud Storage, or Azure Blob, are used to store files, backups, and sensitive data. But if these storage buckets aren’t configured properly (e.g., left public by accident), anyone on the internet can access them. The same logic applies to data warehouse and data lake providers.
In fact, in 2025, 82% of cloud breaches were linked to misconfigured services, with 23–31% of incidents traced to human error.

2. Exposed APIs and Endpoints
APIs are the connection points between apps. In the cloud, they enable systems to communicate with each other.
But if these APIs aren’t secured with proper authentication, encryption, or rate limits, hackers can find them, flood them with requests, or even steal data.
3. Shadow Cloud Assets
Sometimes teams spin up cloud servers, apps, or databases without telling IT. These “shadow assets” don’t follow the same security checks and often go unnoticed or unpatched. Hackers look for these forgotten assets because they’re easy to exploit.
Studies show that 41% of employees use cloud apps and systems which are unknown to their IT department.

4. Insecure Identity and Access Management (IAM)
IAM controls who can access what is inside your cloud environment. Problems happen when users have more permissions than needed, or when Multi-Factor Authentication (MFA) is not enforced. One exposed account can let attackers access more than they should.
5. Credential Leaks and Hardcoded Secrets
Sometimes developers accidentally leave passwords, API keys, or tokens inside code and push them to public platforms like GitHub. Once leaked, attackers can use those credentials to log into cloud environments without even hacking anything.
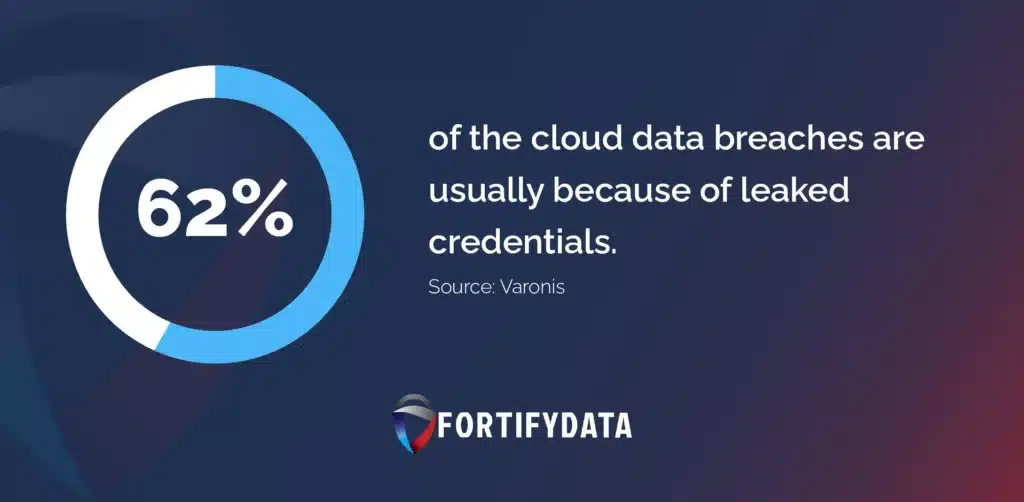
According to Varonis, 62% of the cloud data breaches that don’t involve any human error or physical action are usually done through leaked credentials. This shows how damaging these leaks could be for companies.
How to Mitigate Cloud Attack Surface Risks
Even though there are risks involved in using cloud services, here’s how you can mitigate them with ease:
1. Start with Cloud Attack Surface Management (CASM)
Cloud Attack Surface Management is the continuous process of discovering, monitoring, and securing everything your organization runs in the cloud that attackers could see and exploit.
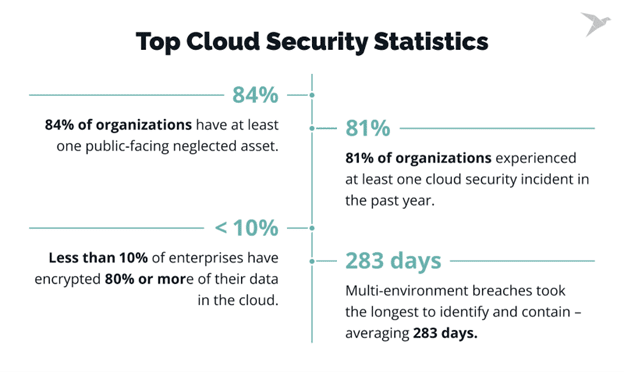
Studies show that 81% of organizations expected at least one cloud security incident in the past year.
This includes storage buckets, APIs, databases, virtual machines, containers, and anything internet-facing. When done right, CASM gives you real-time visibility and control over the overall security attack surface. An often over looked aspect causing undue risk is certificate management. Utilizing a certificate manager secures cloud assets and APIs by encrypting communications, verifying identities, enforcing access controls, and automating lifecycle management. Without it, cloud services and APIs are highly exposed to interception, impersonation, and abuse.
2. Continuous Cloud Asset Discovery
You can’t protect what you don’t see. Many cloud assets get created quickly by different teams, for short-term projects, or through automation. Your Cloud Service Provider (CSP) dashboard may not show everything, especially if it wasn’t provisioned through official channels.
That’s why continuous discovery is essential. Use tools like FortifyData attack surface management to scan and track all your cloud assets, even ones spun up by accident.
3. Cloud IAM Best Practices
Cloud Identity and Access Management (IAM) defines who can access what. The best rule here is “least privilege”, only give users or services the minimum access they need to do their job. Over-privileged accounts are gold for attackers.
By enforcing IAM best practices, organizations can focus on cloud attack surface reduction by minimizing exposed services.
To strengthen IAM:
- Enforce Multi-Factor Authentication (MFA) for all users.
- Rotate keys and passwords regularly.
- Monitor for unusual behavior like access from unknown devices or countries.
- Use identity-based threat detection tools to catch impersonation or lateral movement before it gets costly.
Ready to Regain Control of Your Cloud Attack Surface?
If you’re struggling with blind spots, unclear visibility, or constant alerts you can’t prioritize, it’s time to simplify.
FortifyData’s Attack Surface Management solution gives you a real-time, full-spectrum view of every asset, exposure, and weak point across your cloud environment. We combine asset discovery, misconfiguration detection, and threat intelligence into one unified dashboard.
Start your cloud attack surface management today with FortifyData. Schedule a demo to see how we can help your organization’s cloud security.
FAQs
1. Why is it hard to see all my cloud assets?
Cloud environments grow fast. Teams often spin up resources without centralized oversight (known as shadow IT). Native cloud dashboards don’t always show the full picture, especially across multiple providers or accounts.
2. How do I know if my cloud storage is misconfigured?
The easiest way is to use a Cloud Security Posture Management (CSPM) tool. It automatically checks your storage settings against industry standards and alerts you if buckets are public or unencrypted.