Ever wondered how you can stay ahead when your attack surface keeps growing faster than you can map?
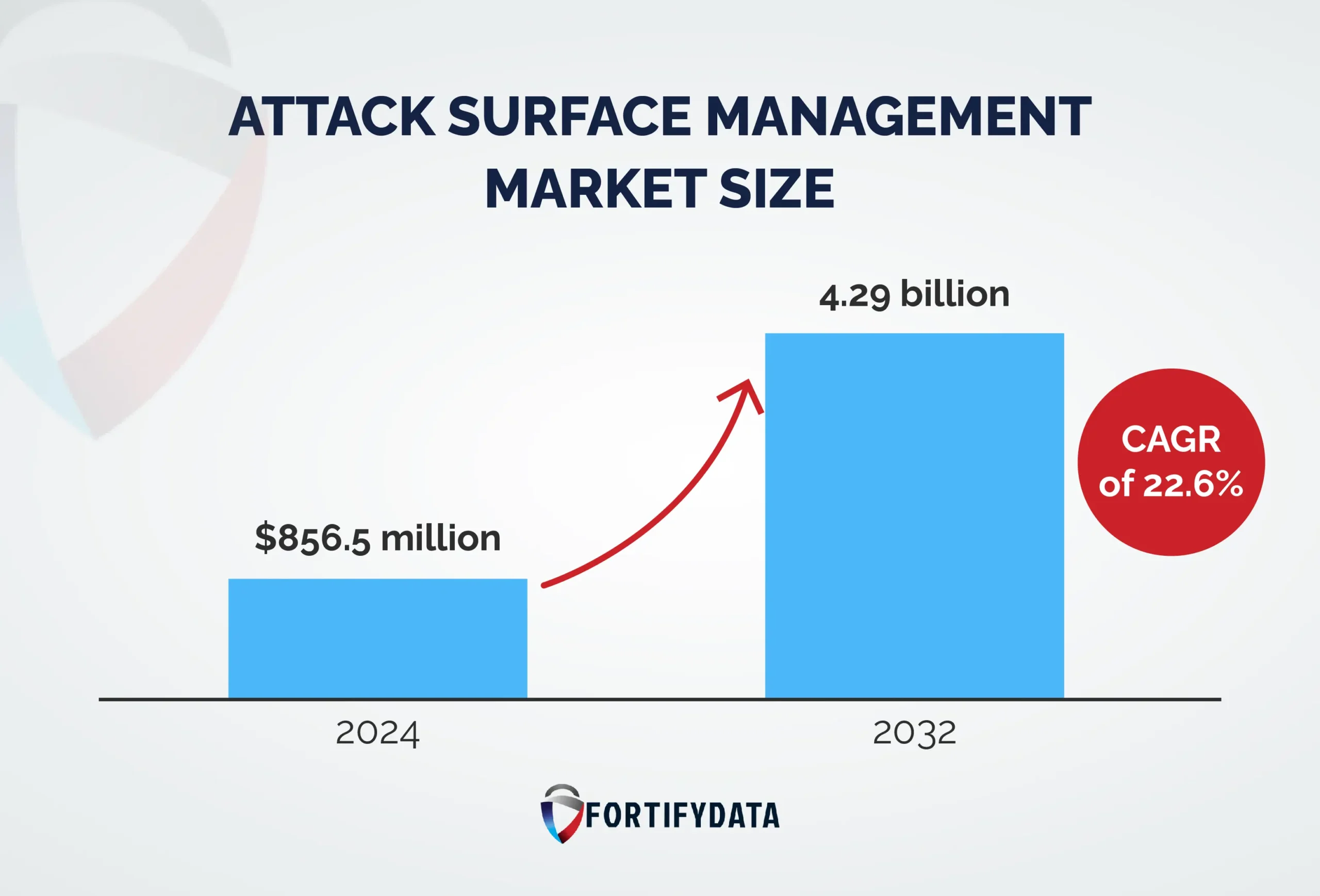
With the Attack Surface Management market size projected to surge from $856.5 million in 2024 to $4.29 billion by 2032, the need for a better ASM strategy has increased.
However, in 2025, building and implementing a scalable Attack Surface Management strategy means combining real-time discovery, intelligent prioritization, and automated remediation to outpace evolving threats. So, are you ready to dig deeper? Keep reading to master this essential strategy
Four Core Pillars of a Scalable ASM Strategy
A strong ASM framework relies on continuous visibility, prioritized vulnerability management, and seamless integration into existing security processes.
1. Continuous Asset Discovery Across All Environments
A scalable Attack Surface Management (ASM) program begins with continuous asset discovery across on-premises, cloud, and hybrid environments.
Without a live inventory of assets, shadow IT and unmanaged endpoints can go unnoticed, creating exploitable entry points. 73% of security leaders experienced incidents caused by unknown or unmanaged assets.
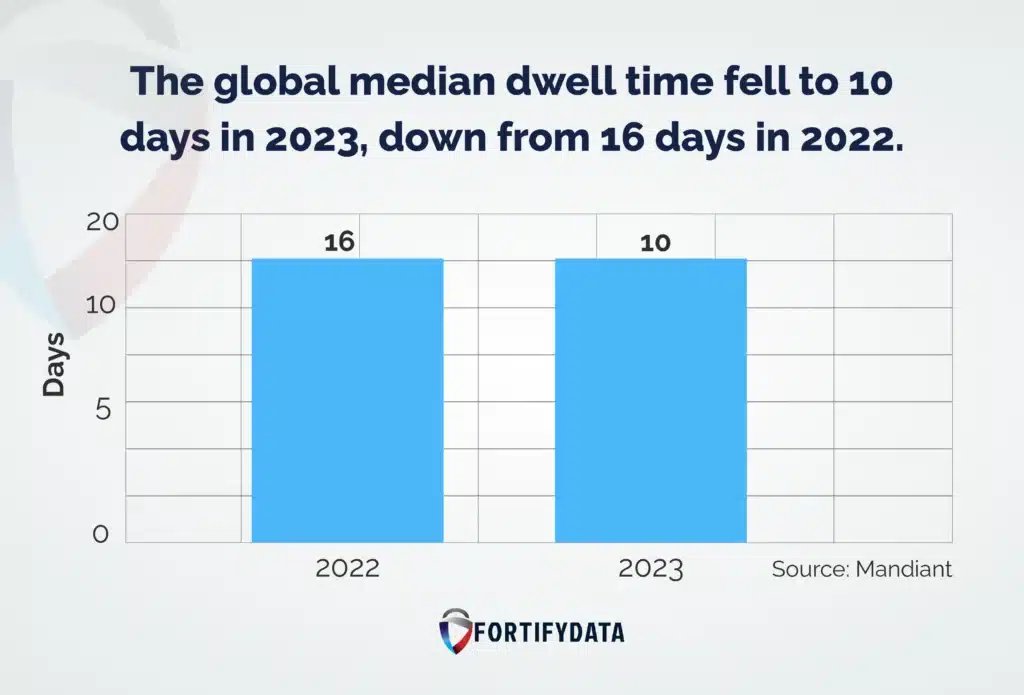
Mandiant’s M-Trends 2024 report shows the global median dwell time of threat actors that have gained unauthorized access fell to 10 days in 2023, down from 16 days in 2022, the lowest in over a decade.
How FortifyData Does This:
- Builds a full inventory of domains, IPs, cloud instances, APIs, and applications tied to your organization without manual input, including Subsidiary and Department organization.
- Automatically discovers and monitors all internet-facing assets—including known, unknown, and shadow IT—on an ongoing basis.
- Performs asset discovery without deploying agents, scaling easily across cloud, hybrid, and global infrastructures.
- Identifies when new assets appear, configurations change, or systems go offline—alerting security teams.
2. Risk-Based Vulnerability Prioritization
Not all vulnerabilities carry equal risk. Vulnerability management must move from patch-all approaches to context-driven prioritization. This means considering asset criticality, exploit availability, and business impact.
Scoring models that combine CVSS data with real-time threat intelligence and business context ensure that the most critical vulnerabilities are addressed first, reducing exposure windows.
How FortifyData Does This:
- Classifies discovered assets by geography, business unit, and criticality, making the footprint meaningful and actionable.
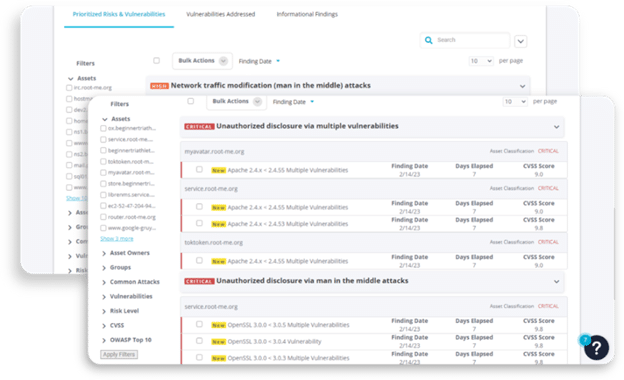
- Enriches discovered assets with vulnerability data, KEV exposure, and exploit intelligence to assess risk relevance.
- Monitors and reports on vulnerabilities, time to remediate, patching cadence
3. Automation in Threat Detection and Response
Scalability requires automation in detecting anomalies and orchestrating responses. AI-driven analytics can identify patterns that human analysts may overlook. Automated workflows for common incidents reduce manual effort, lower response times, and minimize human error during high-pressure events.
How FortifyData Does This:
- FortifyData ingests many cyber threat intelligence feeds to enrich the findings for appropriate risk identification and prioritization based on your inventory
4. Integration with Existing Security Workflows
ASM should complement existing SIEM, SOAR, and CyberGRC systems. Integrating ASM alerts into ticketing and incident management tools ensures that vulnerabilities flow directly into remediation pipelines. This helps align vulnerability remediation with broader security and compliance workflows.
How FortifyData Does This:
- Native integration with other FortifyData modules: Risk and Compliance (GRC), Third-party Risk management and Reporting Suite. Integrations with other tools available.
- Native task collaboration feature to expedite team communication
- Integrations with other tools available
Tools for Creating a Scalable ASM Strategy
Modern ASM solutions use AI, automation, and hybrid deployment models to map, monitor, and protect dynamic attack surfaces in real time.
Read more – How to Evaluate an Attack Surface Management Tool: 7 Must Have Features.
AI-Driven Attack Surface Mapping
Many ASM tools employ artificial intelligence and/or machine learning to correlate asset data, vulnerabilities (asset, code and/or application based), provided business context and threat intelligence to build a real-time map of an organization’s digital footprint. This approach uncovers hidden dependencies, enhances internal risk assessment accuracy, and reveals previously unknown attack vectors.
Cloud-Native and Hybrid ASM Solutions
A modern ASM strategy must work seamlessly across multi-cloud, hybrid, and on-premises environments. Cloud-native solutions offer scalability and speed, while hybrid models allow monitoring of both cloud and on-premises infrastructure without gaps in visibility.
FortifyData: An All-in-One ASM and Risk Management Platform
FortifyData combines ASM, vulnerability management, CyberGRC, and continuous internal risk assessment in a unified platform. Its capabilities include:
| Feature | Benefit |
| Continuous Asset Discovery | Eliminates blind spots across cloud and on-premises |
| Risk-Based Prioritization | Focuses resources on the most dangerous vulnerabilities |
| Remediation Recommendations | Reduces the mean time to respond to incidents |
| CyberGRC Integration | Aligns ASM with compliance requirements |
Real-Time Monitoring vs. Periodic Scans
Periodic scans are no longer enough in dynamic environments where assets can be deployed or decommissioned within hours. Real-time monitoring ensures vulnerabilities and misconfigurations are flagged the moment they appear.
This helps reduce the average attacker dwell time, which was 16 days in 2024 , by enabling faster detection and remediation.
Measuring ASM Effectiveness
Tracking metrics like asset coverage, Mean Time to Detect (MTTD), and Mean Time to Remediate (MTTR) helps validate ASM performance and guide continuous improvement efforts.
Key Performance Indicators (KPIs) for ASM
Strong ASM programs measure their success using metrics such as:
- Asset Coverage Rate: % of assets under continuous monitoring.
- High-Risk Vulnerability Remediation Rate: % of top-tier vulnerabilities resolved within SLA; not just CVSS based, but on critical ‘crown jewel’ assets.
Tracking Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR)
Lower MTTD and MTTR numbers indicate a mature and effective ASM approach. Continuous tracking of these metrics helps security teams identify bottlenecks, streamline workflows, and allocate resources effectively.
Continuous Improvement Loops
ASM is not a set-and-forget process. Continuous improvement involves feeding lessons learned from incidents and vulnerability assessments back into asset inventories, detection logic, and remediation processes.
By aligning vulnerability data with evolving threat intelligence, organizations can ensure their defenses adapt as the attack surface changes.
Take Control of Your Attack Surface with FortifyData
Struggling to keep up with a constantly expanding attack surface and growing security gaps?
Building a scalable Attack Surface Management strategy in 2025 means unifying asset discovery, vulnerability management, and risk assessment in one platform.
FortifyData empowers you to stay ahead of evolving threats.
Take control of your security posture with FortifyData’s Attack Surface Management. Our platforms deliver this through continuous monitoring, AI-driven prioritization, and CyberGRC integration.
Get a jump start on your attack surface management strategy, schedule a demo.
FAQs
1: How often should we update our attack surface inventory?
You should update your attack surface inventory continuously or at least weekly. Cloud assets change quickly, and real-time monitoring ensures you catch new vulnerabilities, shadow IT, or misconfigurations before attackers do.
2: What’s the key difference between ASM and traditional vulnerability management?
ASM continuously maps and monitors all external and internal assets, identifying exposures even outside known systems, while vulnerability management focuses on finding and fixing flaws within already-identified assets.






