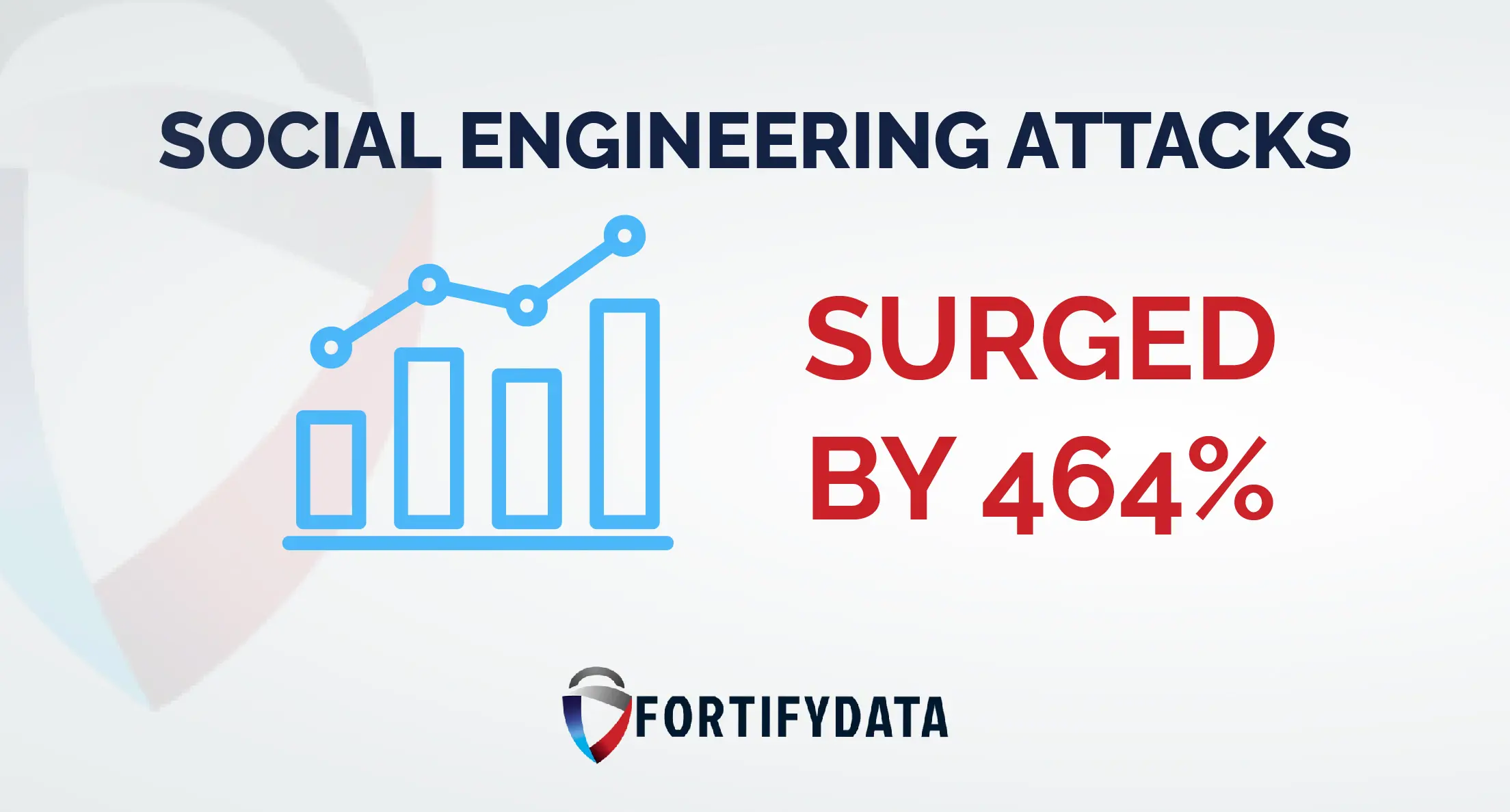
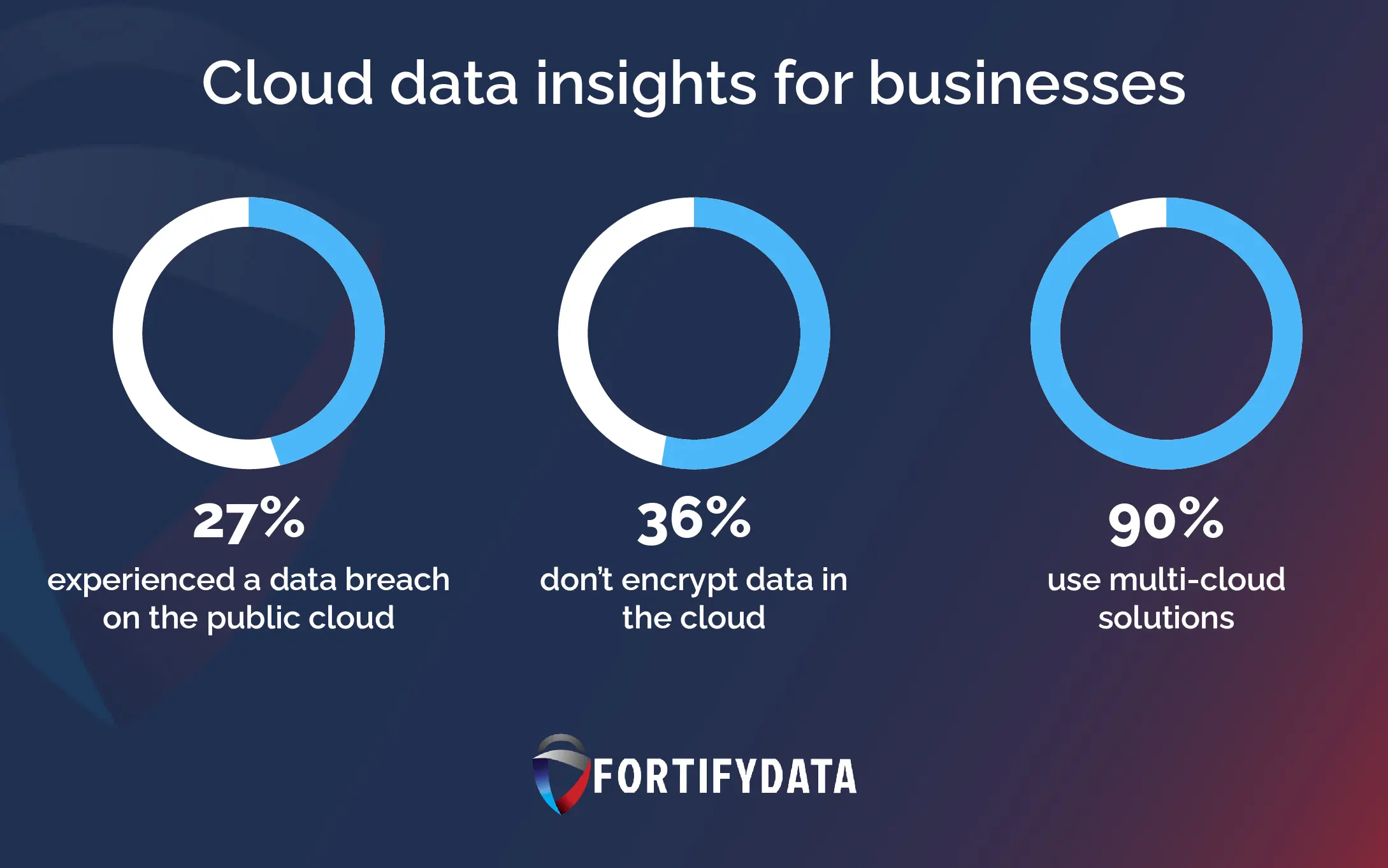
Do you know that in 2024, 3,158 data breaches were recorded in the United States alone? That’s terrifying for businesses.
Most breaches don’t come through the front door; they slip in through overlooked cracks in your digital armor or worse unknown assets tied to other parts of your organization. And many of these breaches happen because of the expanding attack surface due to hybrid working and much more. Even the 2025 Verizon DBIR cited an increase in known vulnerabilities with patches available as a top source for compromise, bucking a downward trend from the previous issues. More on that further below.
As organizations grow more digital, understanding types of attack surfaces in cybersecurity becomes mission-critical. In this article, we’ll break down what the attack surface meaning is, why it matters, and how you can reduce it before attackers find their way in.
So, let’s do that.