Future of TPRM: From Process Management to Autonomous Risk Intelligence
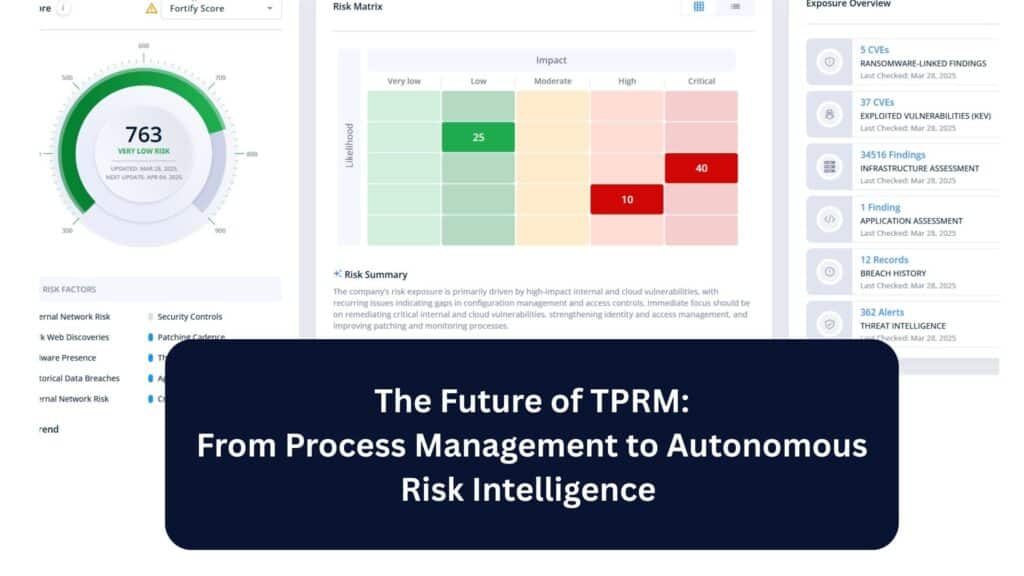
The Future of TPRM: From Process Management to Autonomous Risk Intelligence For years, third-party risk management has been defined by manual effort, periodic assessments, and an uncomfortable tradeoff between speed and confidence. Security teams chase questionnaires. Vendors respond with static documents. Risk is assessed at a moment in time, then quickly becomes outdated. Even as […]
How to Implement a CTEM Security Program in Your Organization

Want to build a CTEM security program that actually works? Learn the steps to build continuous protection and stay ahead of cyber threats.
Automating Trust — How FortifyData Reinvents Third-Party Cyber Risk Management
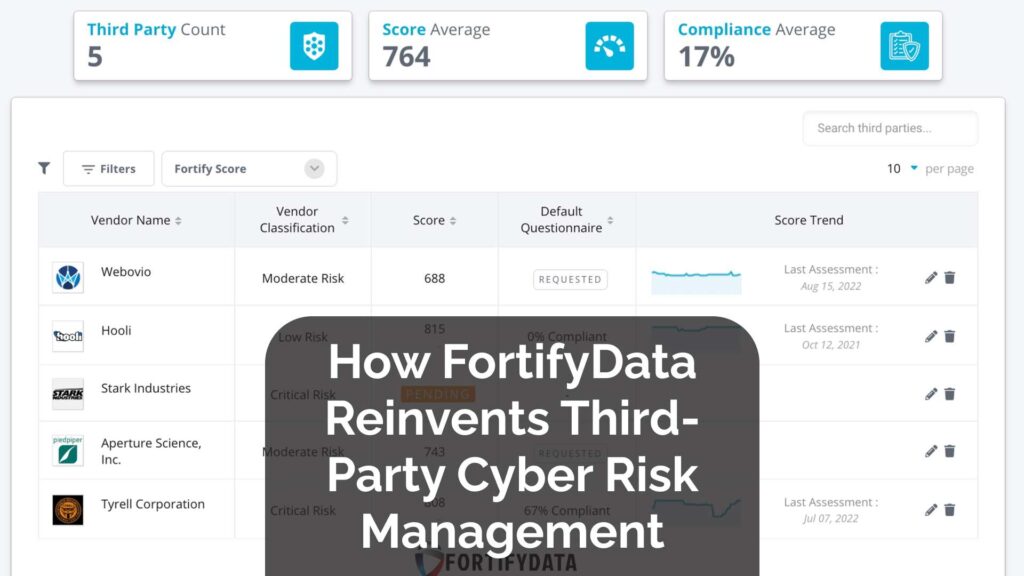
Explore how FortifyData reinvents third-party vendor risk management with AI and automation.
The CTEM Framework: Core Pillars Every Organization Should Know
Wondering what makes CTEM framework powerful? Discover its core pillars and learn how organizations can strengthen cybersecurity with this modern approach.
Introducing FortifyData’s Incident Management Module: From Chaos to Clarity
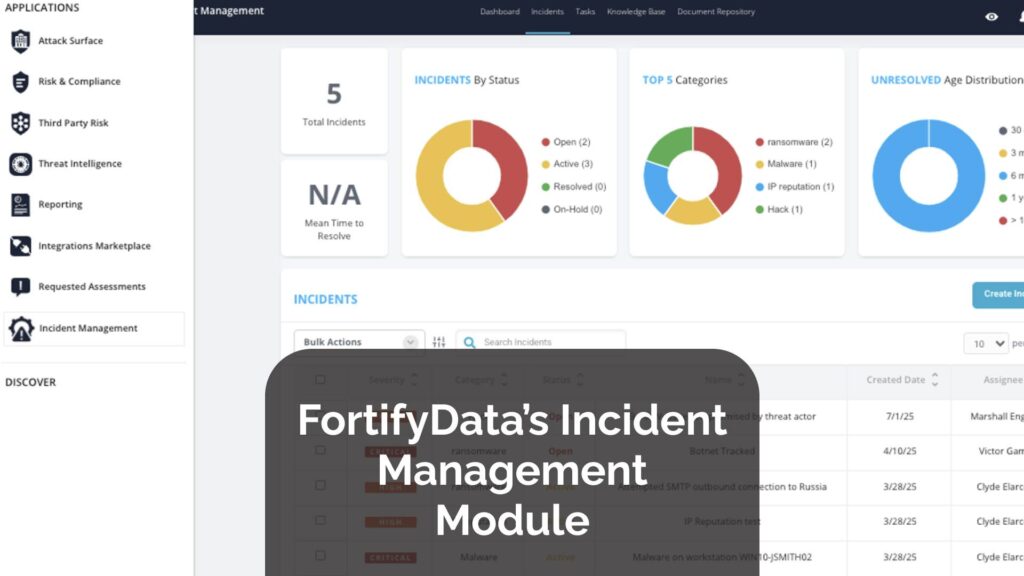
Streamline incident response with FortifyData’s incident management module—log, track, and resolve incidents faster while staying audit-ready and compliant.
Continuous Threat Exposure Management vs Traditional Threat Management: Key Differences

Not sure what sets continuous threat exposure management apart from traditional threat management? Explore key differences to boost security and reduce cyber risks.
FortifyData’s CAASM Capabilities: Full Asset and Exposure Awareness

Want complete visibility of your organization’s assets? Discover how FortifyData’s CAASM capabilities help you find assets, assess every risk, and close every gap.
Top 7 Reasons CISOs Choose FortifyData for Attack Surface Visibility

Wondering why CISOs trust FortifyData for attack surface visibility? Discover seven powerful reasons it stands out in protecting organizations from hidden cyber risks
Building a Scalable Attack Surface Management Strategy in 2025

Outpace evolving threats—learn how to scale your Attack Surface Management strategy and safeguard digital assets.
5 Tips for Eliminating Attack Surface Blind Spots

Discover five practical tips to eliminate attack surface blind spots, strengthen security visibility, and reduce cyber risk across your organization.
