When a cybersecurity incident strikes, speed and structure make all the difference. Yet too often, teams fall back on ad hoc responses, email threads, or general IT ticketing systems to manage what should be a structured, auditable process.
FortifyData’s new Incident Management Module was built to change that. Designed to follow the NIST 800-61 guidelines (provides best practices for managing computer security incidents), this module gives security teams a standardized way to log, analyze, and resolve incidents while improving communication, tracking KPIs, and preserving evidence for compliance.
Why Organizations Need Incident Management
Without a structured process, incident response quickly becomes chaotic. Analysts may scramble to contain the issue, but there’s little consistency in how incidents are logged, tracked, or documented. This creates:
- Delays in containment and recovery.
- Missed opportunities to learn from past events.
- Gaps in audit evidence, increasing regulatory and insurance risks.
As one our product lead put it during the walkthrough:
“Incident management turns chaos into a repeatable, auditable response that cuts time to contain and reduces business impact—while meeting regulatory expectations.”
What the Module Delivers
1. Incident Logging & Intake
Every incident—big or small—can be captured and logged. Unlike ticketing systems that require workarounds, this module ensures incidents are recorded consistently from the moment they’re identified.
2. Classification, Prioritization & Routing
Teams can apply business rules to categorize incidents, assign severity and urgency, and automatically route them to the right resolver group. No more manual juggling of spreadsheets or emails.
3. Communication & Collaboration
Real-time notifications (email, SMS) keep stakeholders and response teams aligned without overwhelming analysts. Status updates are automated, so communication doesn’t become a bottleneck.
4. Knowledge Integration
The module links to past incidents, known error articles, and resolution steps. That means analysts can reuse proven fixes instead of reinventing the wheel.
“A lower-level incident today could be linked to something catastrophic tomorrow. Documenting everything creates the visibility needed for lessons learned and future investigations.”
5. SLA & Metrics Tracking
Dashboards display key metrics like:
- Mean Time to Acknowledge (MTTA)
- Mean Time to Resolve (MTTR)
- SLA compliance
This provides both operational visibility and management reporting, with evidence to support cyber insurance and audit requirements.
6. Post-Incident Review & Documentation
Beyond resolution, the module captures root causes, remediation steps, and links to related problem or change management processes. Supporting files, screenshots, and malicious artifacts can all be stored alongside the incident record.
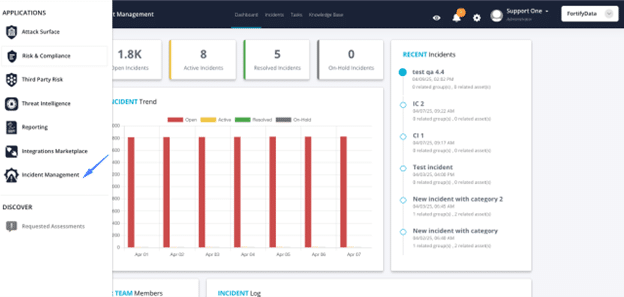
Why Not Just Use a Ticketing System?
Many organizations try to adapt general IT ticketing systems for incident response. But as our team emphasized during the Q&A:
“Ticketing systems aren’t auditable and lack a standard approach for tracking incidents. FortifyData’s module follows NIST 800-61, covering detection through recovery, and makes the process easily auditable for regulators and insurers.”
In other words: incident management isn’t just another ticket—it’s a specialized, compliance-critical process.
Meeting Organizations Where They Are
The module is designed to support teams of all maturity levels:
- For organizations with no formal incident response plan, it provides an immediate, structured starting point.
- For more advanced teams, it integrates with existing FortifyData modules (attack surface, vulnerability, vendor risk) and external tools like Microsoft Defender or SIEM platforms to streamline workflows.
“This module allows organizations without an existing process to quickly start managing incidents effectively. And for advanced teams, it centralizes intake, orchestrates actions, and preserves evidence—even when no SIEM is involved.”
The FortifyData Difference and Value of Consolidation
FortifyData’s Incident Management Module isn’t a standalone add-on. It’s part of a unified Cyber GRC platform that already delivers:
- Attack Surface Management
- Vulnerability Management
- Third-Party Risk Management
- Compliance Framework Mapping and Automation
By embedding incident management alongside these capabilities, organizations gain one source of truth for cybersecurity risk, compliance, and incident response.
Reach out to schedule a demo for our Incident Management module or Cyber GRC platform as a whole.
Orchestrated Response with Incident Management Software
Incidents will happen. The question is whether your organization responds with ad hoc scrambling or a structured, auditable process that reduces downtime, preserves evidence, and strengthens compliance.
With FortifyData’s Incident Management Module, security teams can replace chaos with clarity—logging every incident, prioritizing effectively, collaborating in real-time, and learning from the past to prepare for the future.