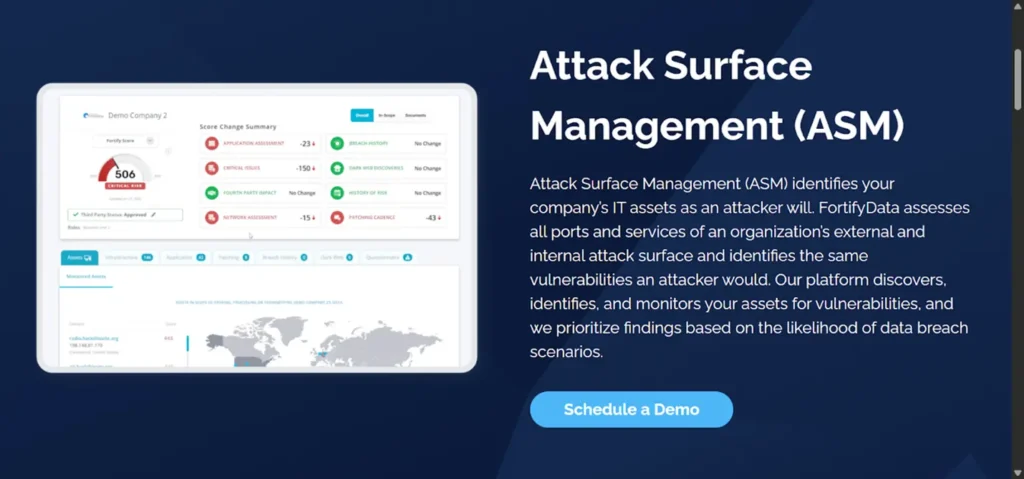
Organizations attack surfaces continue to expand. With hybrid work, cloud sprawl, shadow IT (also shadow AI), constant code changes, and increasing third-party connections, organizations today face more external risks than ever before. In fact, studies show that 73% of security breaches now originate from unknown or unmanaged assets.
This is where Attack Surface Management tools come in. These platforms continuously scan, monitor, and help secure all internet-facing assets tied to your organization, from forgotten subdomains, insecure storage buckets, wide-open databases, to exposed APIs.
In this guide, we’ll walk you through the top 11 Attack Surface Management solutions in 2025, what they offer.