Have you ever wondered how hackers actually break into companies?
Most of the time, it’s something shockingly boring. They just find something exposed that no one noticed. And that’s worse than it sounds.
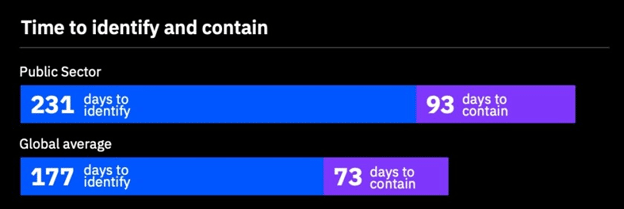
In fact, in 2024, IBM reported that the average data breach cost businesses $4.45 million.
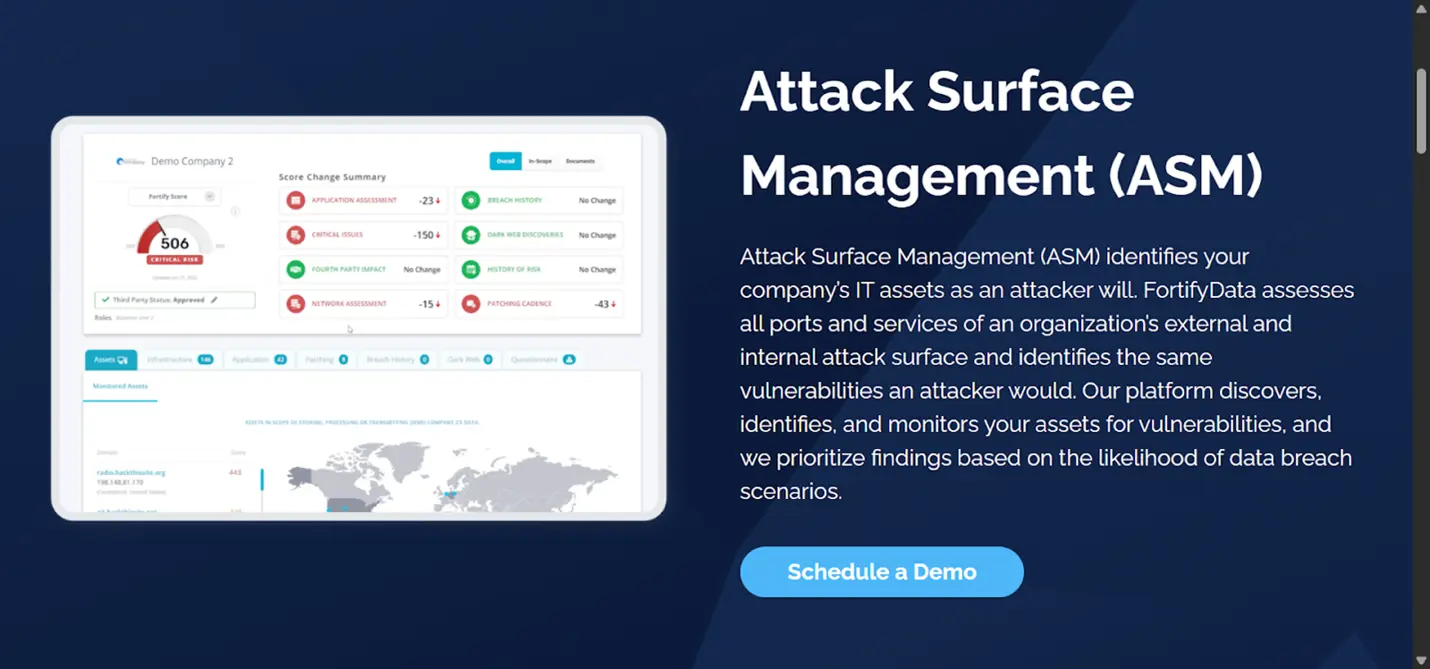
One of the best ways to be proactive with cyber defense is with an Attack Surface Management (ASM) program. It’s like walking around the house every day, checking every entry point before someone else does.
Sounds obvious, right? But you’d be surprised how many companies skip it or difficult to keep with as different business units procure services or spin up assets.
So, to make sure you don’t do that to your company, here’s what attack surface management is and everything else you need to know about it.